LockBit Ransomware Tests Taking a Bite Out of Apple Users
Data Breach Today
APRIL 17, 2023
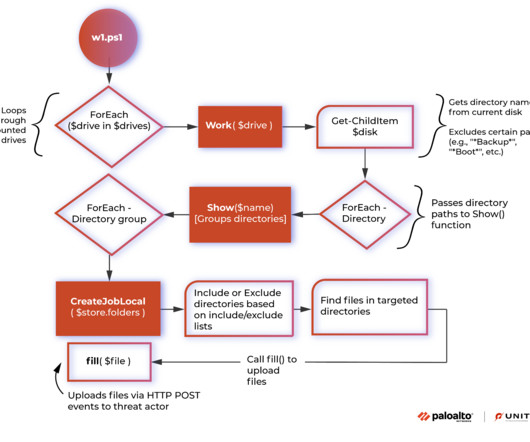
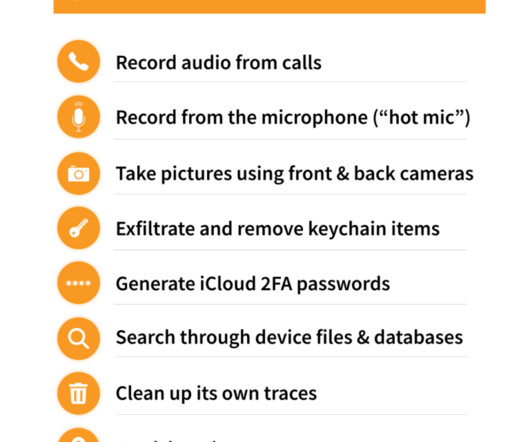
Don't Panic: Apparent macOS Beta Testing Is Highly Buggy, Poses No Immediate Threat Apple users: Don't fear newly discovered samples of LockBit ransomware designed to target newer macOS devices. Researchers say the still-in-development code, tied to no known in-the-wild attacks, contains numerous errors, leaving it unable to execute.







































Let's personalize your content