Alert: Chinese Malware Targeting IT Service Providers
Data Breach Today
AUGUST 4, 2020
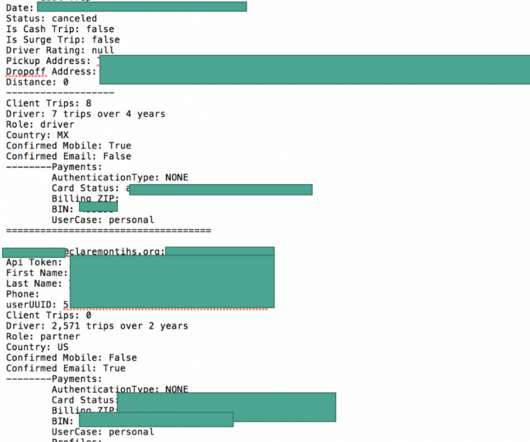
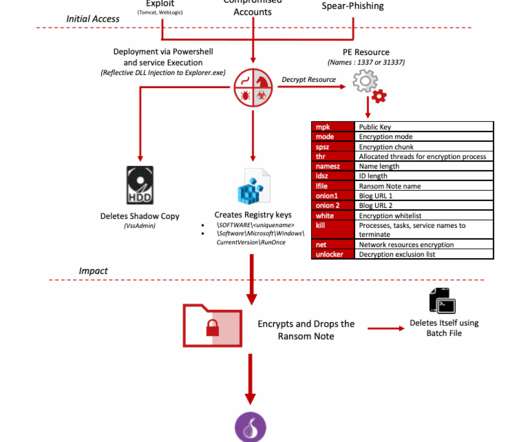
CISA, DOD, FBI Issue Warning About Campaign Using Taidoor RAT A trio of U.S. government agencies is warning organizations about a hacking campaign using a malware strain that has previously been tied to Chinese hackers. The Taidoor RAT, which has been around for over 10 years, has recently been spotted in several campaigns against IT service providers.






































Let's personalize your content