Inside the Rise of 'Dark' AI Tools - Scary, But Effective?
Data Breach Today
AUGUST 17, 2023
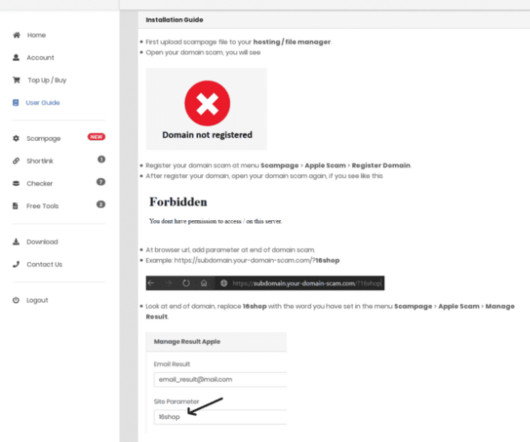
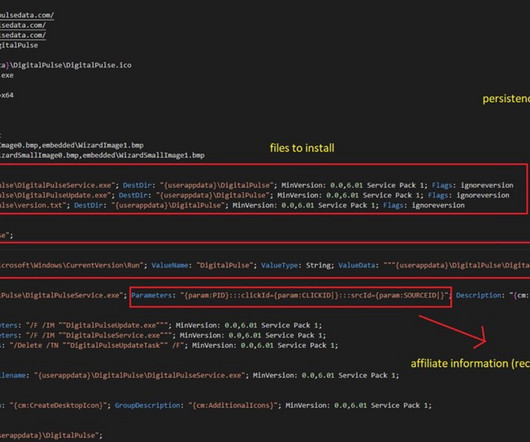
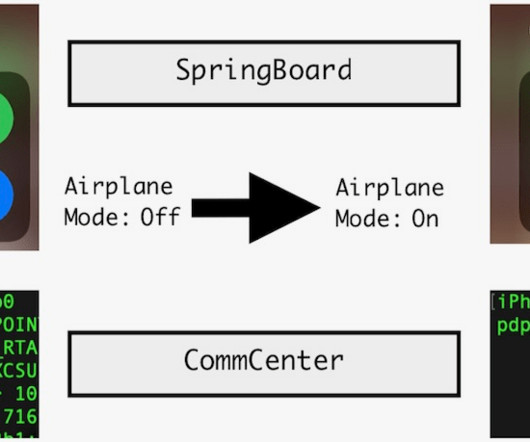
WormGPT, DarkGPT and Their Ilk Underdelivered - or Were Scams, Researchers Report Various "dark" generative artificial intelligence tools purportedly help criminals more quickly amass victims. Guess what? They've all gone bust, if they weren't simply outright scams - in part because legitimate tools can be "jailbroken" to achieve similar results. What are they really achieving?




































Let's personalize your content