EU Will Stand Up Office to Enforce AI Act, Says EU Lawmaker
Data Breach Today
OCTOBER 16, 2023
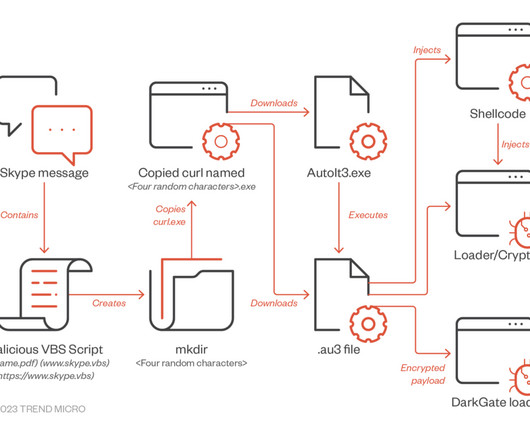
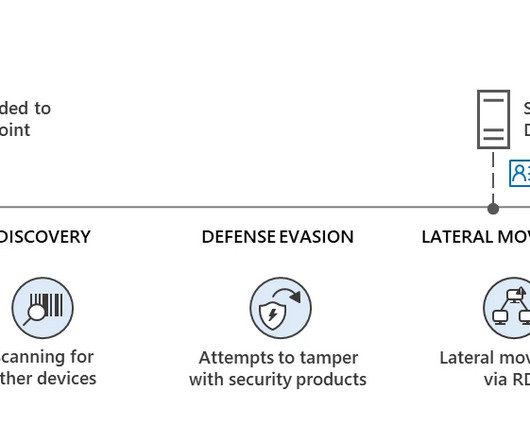
Dragos Tudorache Says the Agency Will Be a "Powerful Enforcer" of AI Act The EU will set up a dedicated office to oversee the implementation of the AI Act, especially by big-tech companies such as OpenAI. Dragoş Tudorache, a Romanian politician and the co-rapporteur of the AI Act, said negotiators have agreed in principle on creation of an "EU AI Office.







































Let's personalize your content