CISA's New 'CyberSentry' Program to Tighten ICS Security
Data Breach Today
JULY 3, 2023
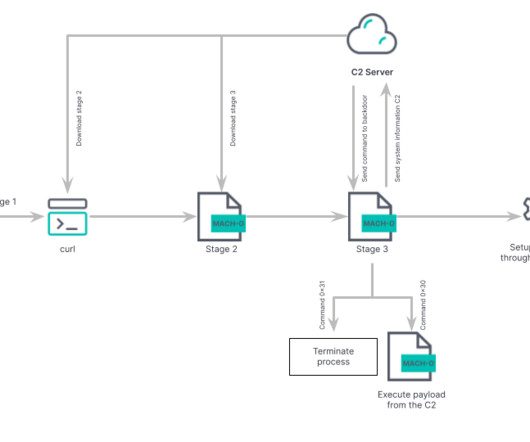
Program to Monitor IT, OT Networks of Enrolled Critical Infrastructure Partners The United States is further fortifying its critical infrastructure security with a new Cybersecurity and Infrastructure Security Agency program that enhances the cyber resilience of participating partners leveraging the agency's advanced threat detection and monitoring capabilities.





































Let's personalize your content