Breach Roundup: CIA Hacking Tool Leaker Gets 40 Years
Data Breach Today
FEBRUARY 1, 2024
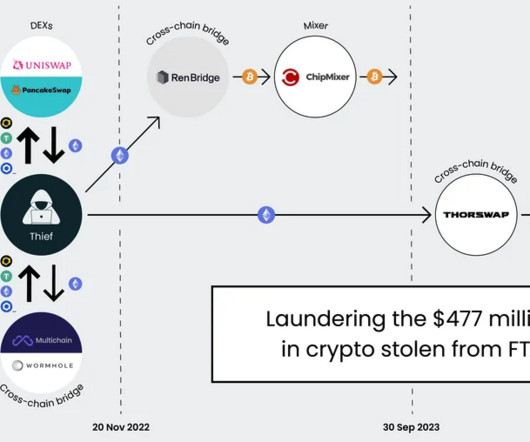
Also: Cloudflare Was Hacked With Stolen Okta Token This week, former CIA programmer gets 40-year sentence, zero trust prevents widespread damage, possible ransomware attack in Georgia, alleged hacker detained in Ukraine, USB-spread malware in Italy, LockBit attack on non-bank home mortgage lender, and Ukrainian critical infrastructure disrupted.








































Let's personalize your content