Tactics for Battling Attacks by Russia's Midnight Blizzard
Data Breach Today
MARCH 20, 2024
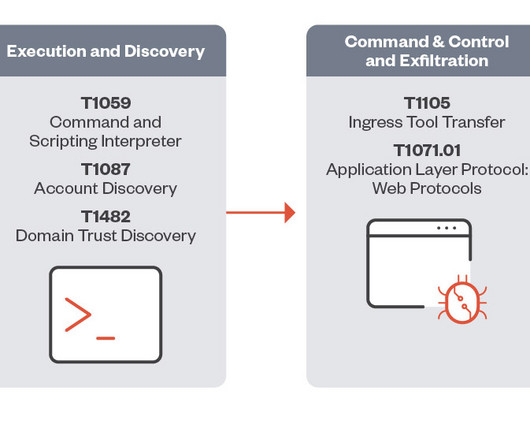
As Nation-State Group Hacks Big Targets, Trellix's John Fokker Details Defenses Major technology vendors keep being hacked by the nation-state hacking group Midnight Blizzard. Essential defenses to combat such attacks begin with implementing log monitoring across multiple platforms to find red flags, said John Fokker, head of threat intelligence at Trellix.









































Let's personalize your content