Breach Roundup: More Fallout From the LockBit Takedown
Data Breach Today
FEBRUARY 22, 2024
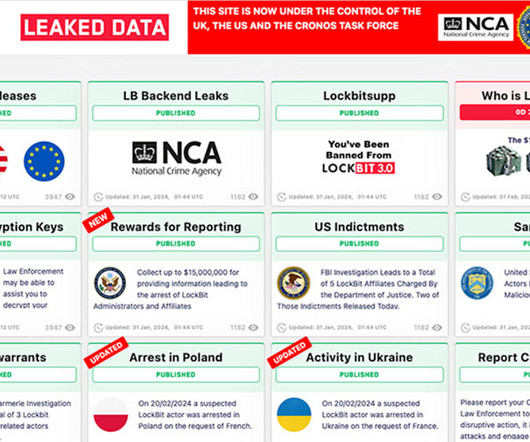
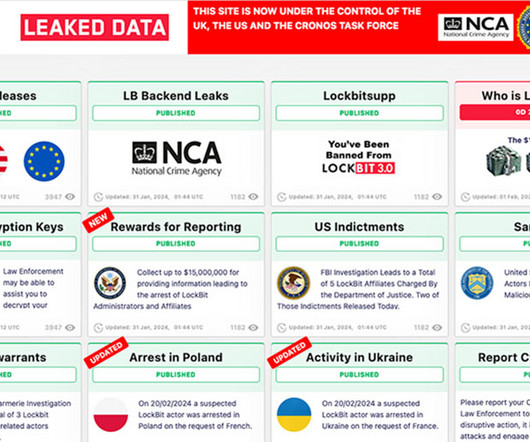
Also: Avast Agrees to $16.5 Million Civil Penalty to Settle Privacy Investigation This week: more fallout from LockBit, Avast to pay $16.5M, Russia-linked group targeted mail servers, no indication that AT&T was hacked, analysis of a patched Apple flaw, Microsoft enhanced logging, an Android banking Trojan, North Korean hackers and a baking giant fell to ransomware.






































Let's personalize your content