Dropbox Used in Latest Exploit for Phishing Attacks
Data Breach Today
MARCH 11, 2024
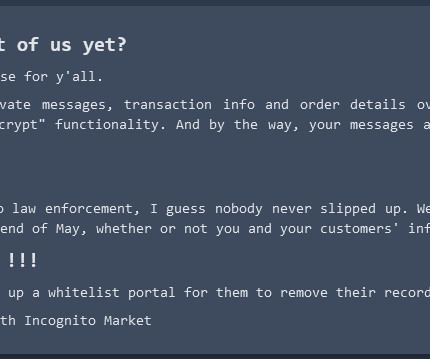
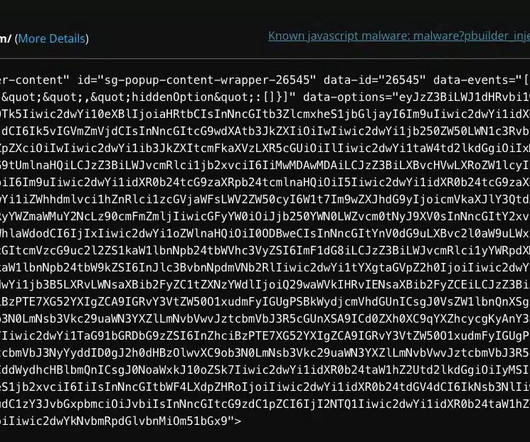
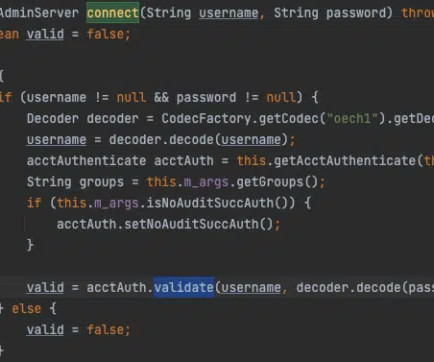
Darktrace Warns of Malware Hidden in PDF Stored in Dropbox Phishing attacks continue to adapt to exploit popular apps. While many phishing campaigns have focused on mobile banking and payment sites, attackers are also targeting widely used but lower-profile, cloud-based utilities such as the ubiquitous Dropbox storage platform.






































Let's personalize your content