Boeing Reports 'Cyber Incident'; Ransomware Group Claims Hit
Data Breach Today
NOVEMBER 2, 2023
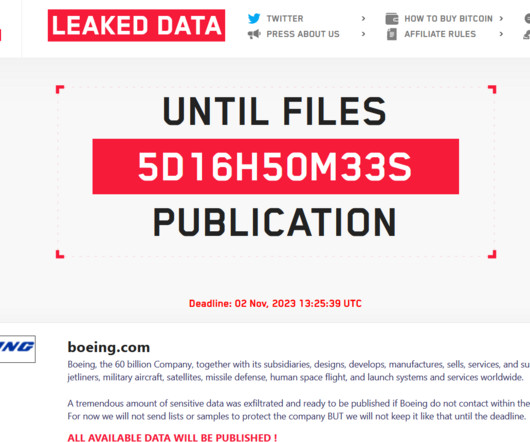
Aerospace Giant Says Elements of Parts and Distribution Business Are Affected Boeing has confirmed suffering a "cyber incident" affecting its parts and distribution business days after the notorious LockBit ransomware group claimed to have breached systems at the world's biggest aerospace company and to have stolen "a tremendous amount of sensitive data.








































Let's personalize your content