Big MGM Resorts Outage Traces to Ransomware, Researchers Say
Data Breach Today
SEPTEMBER 13, 2023
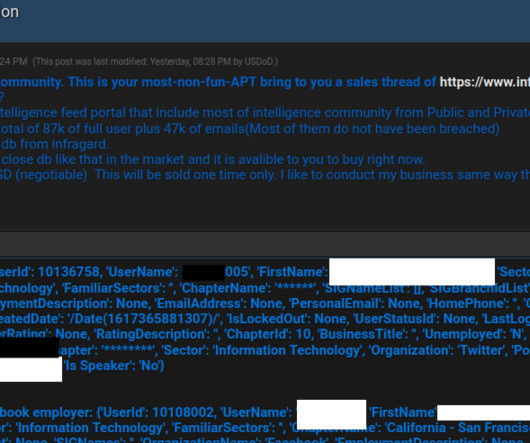
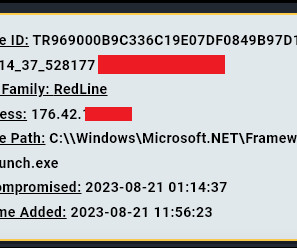
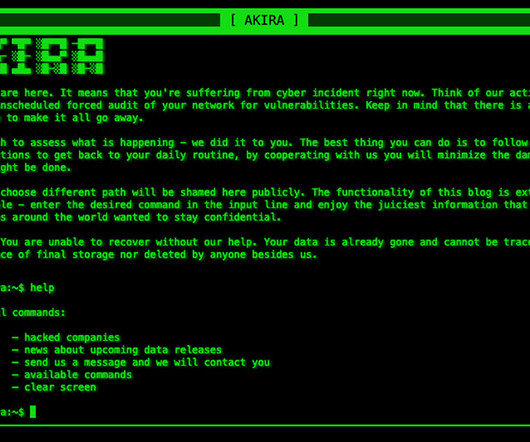
Alphv/BlackCat Group Reportedly Hit Casino Operator via Social Engineering Attack Booking and reservation systems, as well as slot machines, hotel room door locks, ATMs and more remain offline at multiple MGM Resorts properties as the publicly traded casino hotel giant battles "a cybersecurity issue" that one group of security researchers has tied to a ransomware group attack.








































Let's personalize your content