JumpCloud Hackers Likely Targeting GitHub Accounts Too
Data Breach Today
JULY 21, 2023
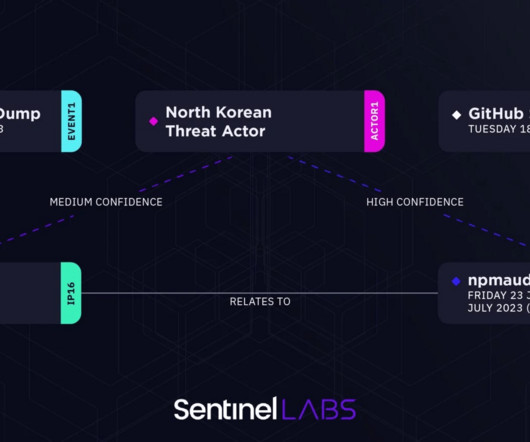
Targets Include Blockchain, Crypto, Online Gambling and Cybersecurity Sectors Suspected North Korean hackers who targeted enterprise software firm JumpCloud are likely behind a social engineering campaign targeting the personal GitHub accounts of employees from major technology firms - including those in the cybersecurity sector.








































Let's personalize your content