E-Commerce Firms Are Top Targets for API, Web Apps Attacks
Data Breach Today
JUNE 13, 2023
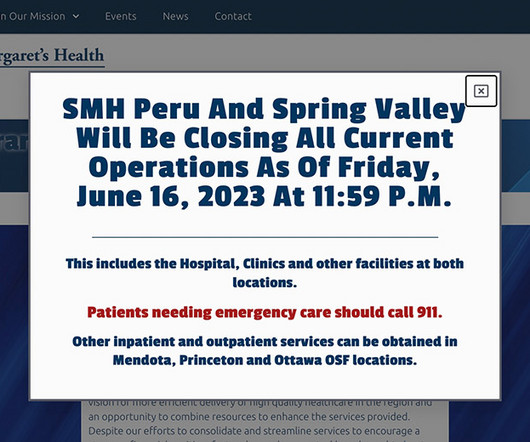
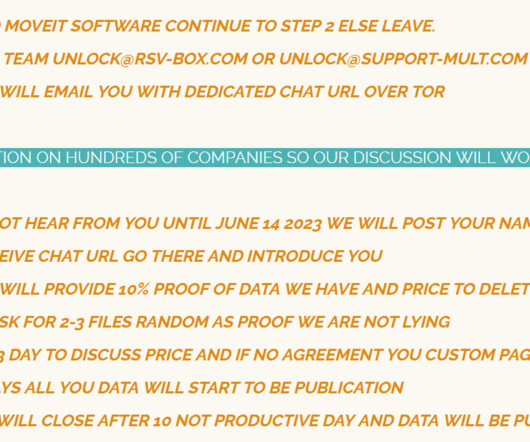
Akamai: Rapid Digitalization, Flawed Code Led to 14 Billion Attacks in Past Year Hackers hit the e-commerce industry with 14 billion attacks in 15 months, pushing it to the top of the list of targets for web application and API exploits. A new Akamai report blames digitalization and the wide range of vulnerabilities hackers can exploit in web applications.








































Let's personalize your content