Breach Roundup: Citrix Patch Not Sufficient
Data Breach Today
OCTOBER 19, 2023
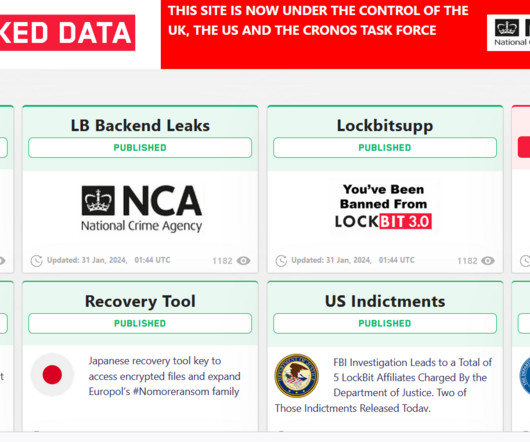
Also: Navy IT Manager Sentenced to 5 Years in Prison for Accessing Database This week, Citrix's update was insufficient, a Navy IT manager was sentenced to prison for accessing a database, a Moldovan man pleaded not guilty to running a credentials marketplace, new details emerged on health data breaches, and a television advertising giant suffered (..)











































Let's personalize your content