Chinese Group Targeting Vulnerable Cloud Providers, Applications
Data Breach Today
JANUARY 21, 2023
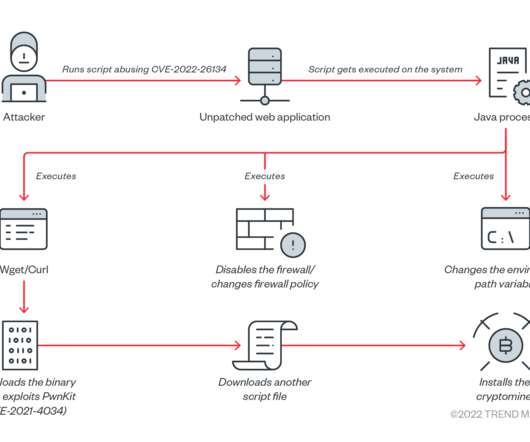
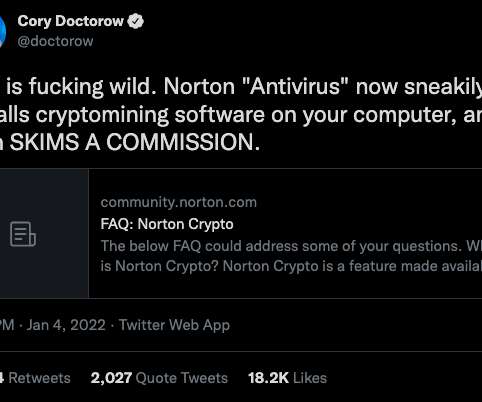
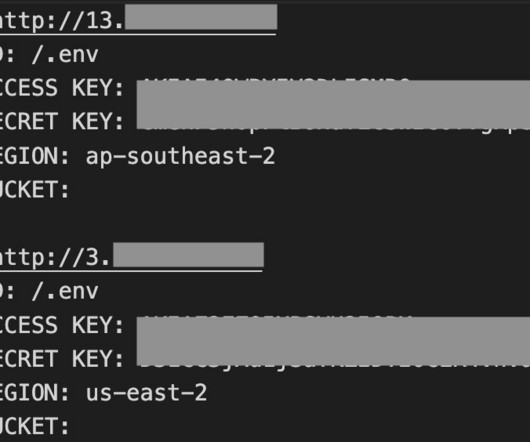
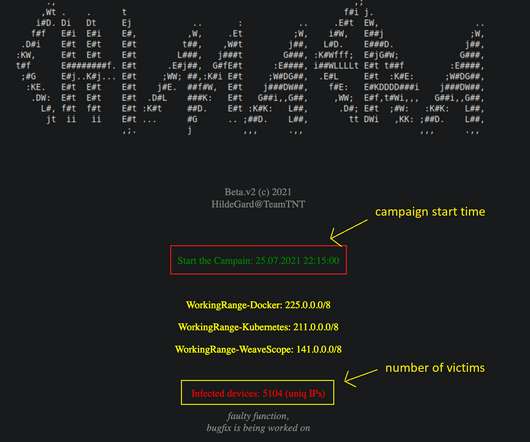
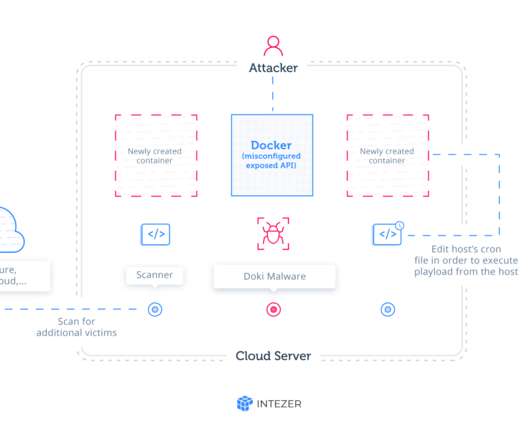
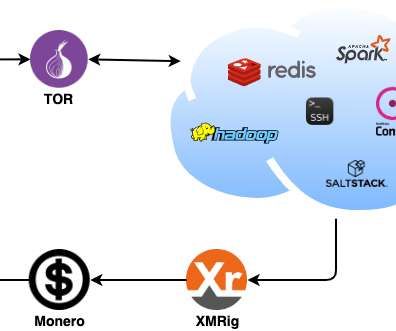
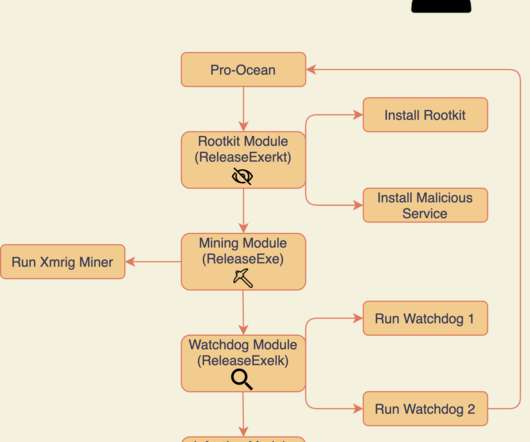
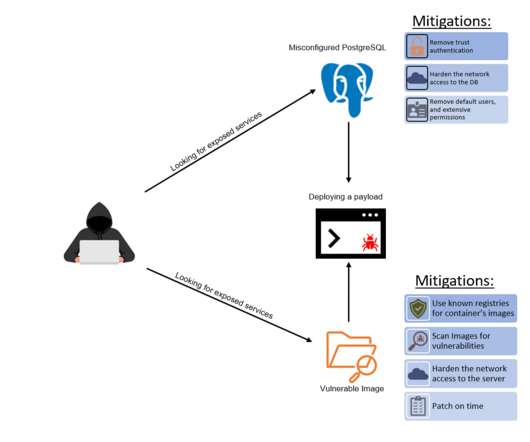
Crypto Mining Campaign Targets Public Cloud Environments, Increases Security Risks Cybersecurity researchers say a Chinese for-profit threat group tracked as 8220 Gang is targeting cloud providers and poorly secured applications with a custom-built crypto miner and IRC bot.





































Let's personalize your content