ESG Research Unearths Critical Insights for Future-Proofing Encryption and Key Management
Thales Cloud Protection & Licensing
JANUARY 31, 2024
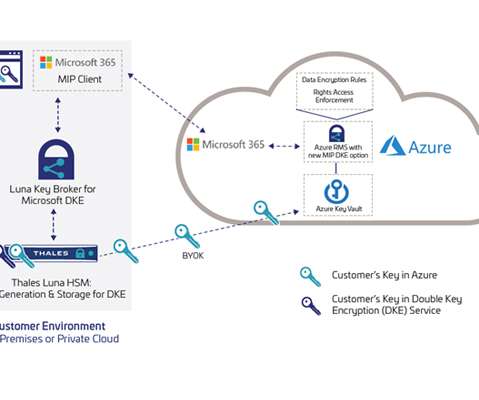
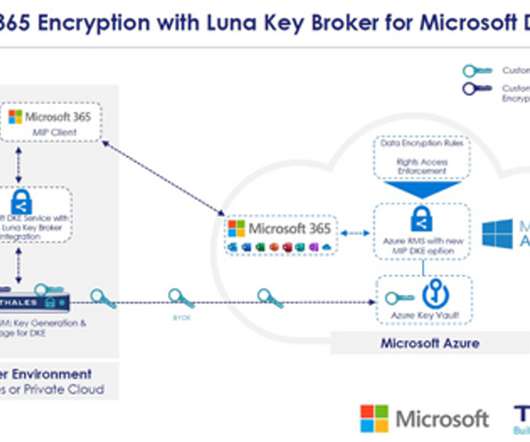
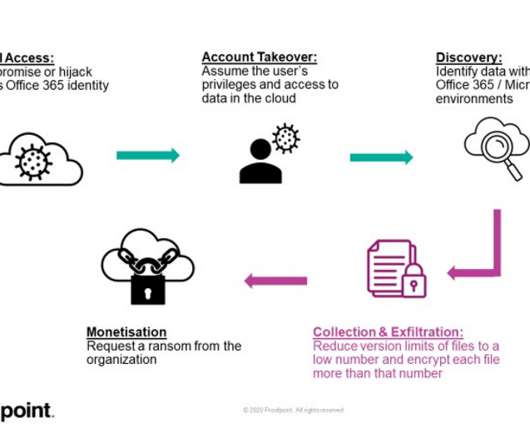
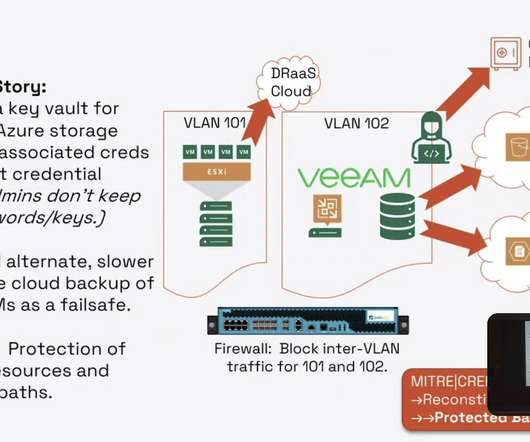
ESG Research Unearths Critical Insights for Future-Proofing Encryption and Key Management madhav Thu, 02/01/2024 - 05:14 Encryption and key management are critical defenses against data breaches and cyber threats in the evolving digital landscape.














































Let's personalize your content