Best Enterprise Network Security Products
eSecurity Planet
AUGUST 4, 2020
Here are some of the best network security software and hardware products to protect vital data. Network security is central to IT security.

 best-products
best-products 
eSecurity Planet
AUGUST 4, 2020
Here are some of the best network security software and hardware products to protect vital data. Network security is central to IT security.

KnowBe4
MARCH 25, 2024
Year after year, the events team manages to keep a fine balance between product updates and thought leadership talks. The convention is the best time to shine for all of us at KnowBe4, and nothing is shinier these days than the promise of an AI-powered future.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
FEBRUARY 20, 2024
In e-commerce, it facilitates smooth product inquiries and order tracking. In customer support, it seamlessly integrates with Microsoft’s ecosystem for enhanced productivity. Examples of AI chatbot platforms include: •Dialogflow: Developed by Google, Dialogflow is renowned for its comprehension capabilities.
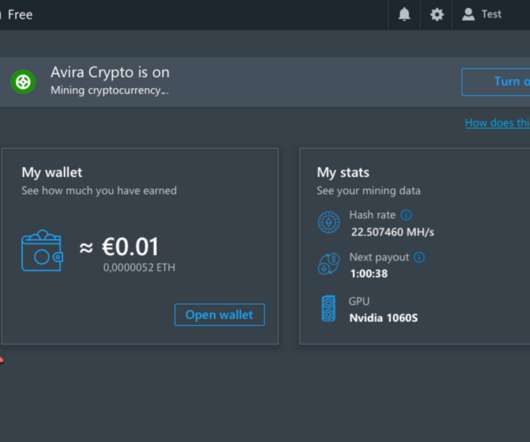
Krebs on Security
JANUARY 8, 2022
But Norton 360 isn’t alone in this dubious endeavor: Avira antivirus — which has built a base of 500 million users worldwide largely by making the product free — was recently bought by the same company that owns Norton 360 and is introducing its customers to a service called Avira Crypto. Avira Crypto.

Advertisement
What are best practices when designing the UI and UX of embedded dashboards, reports, and analytics? What should software teams know about implementing security that works with the rest of their products? What should product managers keep in mind when adding an analytics project to their roadmap?

eSecurity Planet
APRIL 12, 2024
Data loss prevention (DLP) best practices are principles that help prevent intentional or unintentional data erasure. 12 Data Loss Prevention Best Practices A data loss prevention policy lays the groundwork, but the effectiveness of data security hinges on adopting globally accepted best practices.

The Last Watchdog
FEBRUARY 21, 2024
According to DigiCert’s 2024 State of Digital Trust Survey results, released today , companies proactively pursuing digital trust are seeing boosts in revenue, innovation and productivity. The gap between the leaders and the laggards is growing,” says Brian Trzupek , DigiCert’s senior vice president of product. “If

Advertisement
No matter where you are in your analytics journey, you will learn about emerging trends and gather best practices from product experts. We interviewed 16 experts across business intelligence, UI/UX, security and more to find out what it takes to build an application with analytics at its core.

Speaker: Logi Analytics
At this free virtual event, your team will learn practical tips from the pros to help turn your product roadmap into a reality and generate value for your end users. Logi Spark 2021 consists of two days of networking, best practice sessions, and forward-thinking keynotes on the future of data.

Advertisement
Just by embedding analytics, application owners can charge 24% more for their product. This framework explains how application enhancements can extend your product offerings. How much value could you add? Brought to you by Logi Analytics.

Advertisement
Read the 6th annual State of Embedded Analytics Report to discover new best practices. We surveyed 500+ application teams embedding analytics to find out which analytics features actually move the needle. Brought to you by Logi Analytics.

Advertisement
Think your customers will pay more for data visualizations in your application? Five years ago they may have. But today, dashboards and visualizations have become table stakes. Discover which features will differentiate your application and maximize the ROI of your embedded analytics. Brought to you by Logi Analytics.

Advertisement
Many application teams leave embedded analytics to languish until something—an unhappy customer, plummeting revenue, a spike in customer churn—demands change. But by then, it may be too late. In this White Paper, Logi Analytics has identified 5 tell-tale signs your project is moving from “nice to have” to “needed yesterday.".

Speaker: Dr. Greg Loughnane and Chris Alexiuk
Technology professionals developing generative AI applications are finding that there are big leaps from POCs and MVPs to production-ready applications. However, during development – and even more so once deployed to production – best practices for operating and improving generative AI applications are less understood.

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will provide you with best practices for attack prevention and recovery. Ransomware protection planning best practices. Best practices for choosing a DRaaS solution.
Let's personalize your content