Hyperscale vs. colocation: Go big or go rent?
IBM Big Data Hub
MARCH 27, 2024
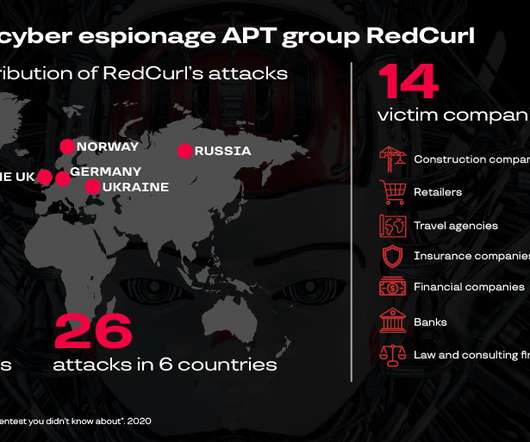
These voices forcefully advocate using a colocation solution, where your company will instead rent space in a hyperscale data center, thus saving USD millions or even billions in construction costs and other associated charges. Development costs to survey the land, clear the site and prepare it for construction. What is colocation?


















































Let's personalize your content