Ransomware realities in 2023: one employee mistake can cost a company millions
Security Affairs
OCTOBER 17, 2023
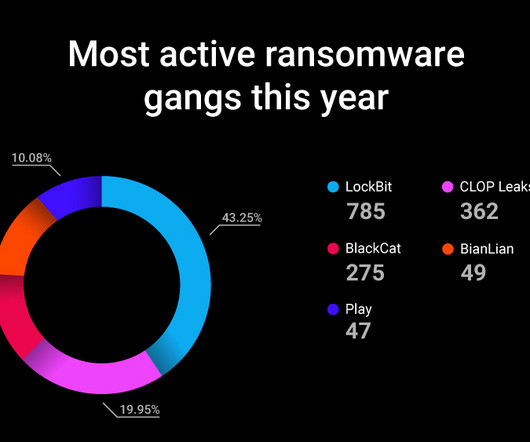
Based on Ransomlooker, a free Cybernews tool for monitoring the dark web and other hidden areas of the internet, 64% of organizations have already suffered from a ransomware attack. This is happening despite an exponential increase in organizational cyber training over the past decade.























Let's personalize your content