Exposed Kubernetes configuration secrets can fuel supply chain attacks
Security Affairs
NOVEMBER 24, 2023
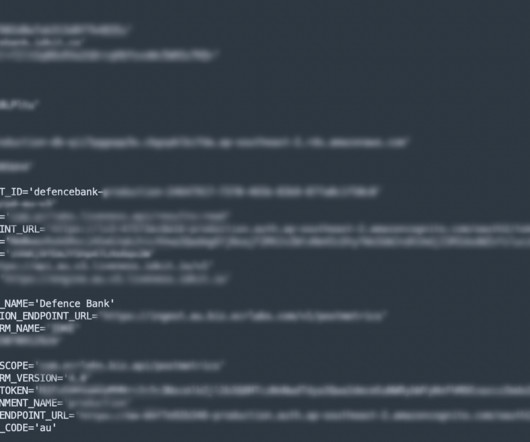
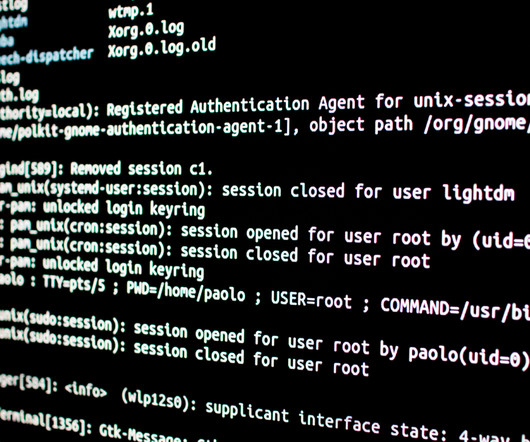
Researchers warn of publicly exposed Kubernetes configuration secrets that could pose a threat of supply chain attack for organizations. The researchers pointed out that most of these credentials provided both pulling and pushing privileges. 203 records contained valid credentials that grant access to the respective registries.



















Let's personalize your content