Cl0p hacker operating from Russia-Ukraine war front line – exclusive
Security Affairs
JULY 12, 2023
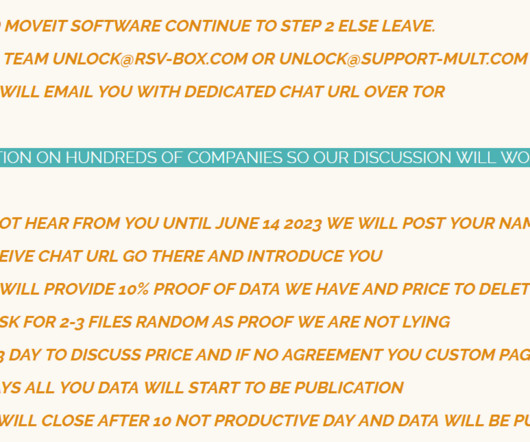
As is quite common with malicious activity en masse, malicious hackers chose the Memorial Day weekend in the US (May 27th and 28th) for a “broad swath of activity.” In June 2021, Ukrainian law enforcement, in collaboration with US and South Korean officials, arrested six Cl0p members and dismantled the gang’s infrastructure.






















Let's personalize your content