How to Use MITRE ATT&CK to Understand Attacker Behavior
eSecurity Planet
DECEMBER 29, 2021
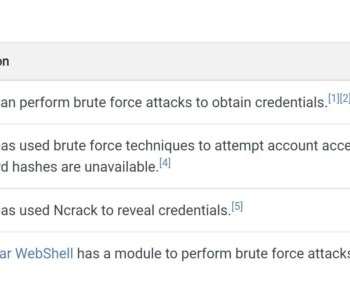
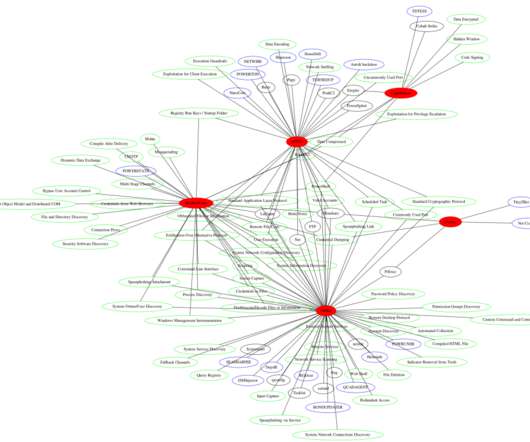
MITRE ATT&CK (“miter attack”) is an up-to-date and widely-used knowledge base that focuses on how attackers think and operate. It’s based on practical use cases, so companies can better evaluate security issues and get examples of common tactics and techniques used by threat actors.






















Let's personalize your content