Implementing and Managing Your SIEM Securely: A Checklist
eSecurity Planet
DECEMBER 17, 2021
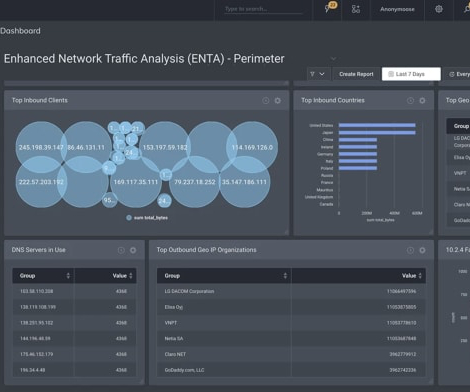
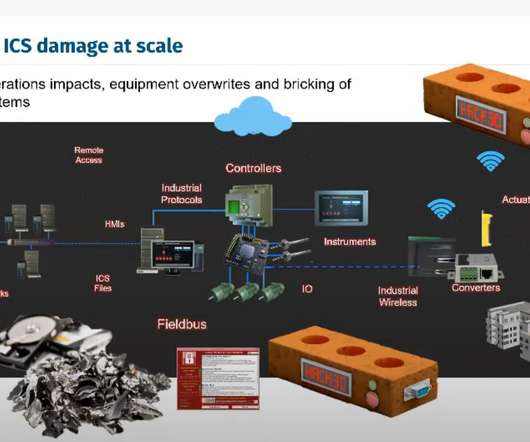
Some companies use cloud-based security information and event management (SIEM) , and others use SIEM that has been installed in a local data center. These on-premises SIEMs can be run on Windows Servers, Linux Servers, and within virtual machines (VMs) or containers. See our picks for the Best SIEM Solutions.




















Let's personalize your content