Voice Phishers Targeting Corporate VPNs
Krebs on Security
AUGUST 19, 2020
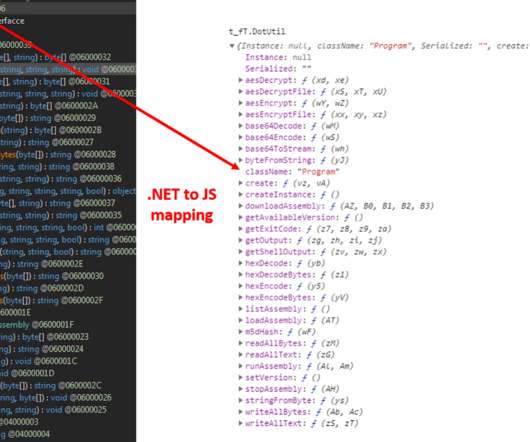
Allen said a typical voice phishing or “vishing” attack by this group involves at least two perpetrators: One who is social engineering the target over the phone, and another co-conspirator who takes any credentials entered at the phishing page and quickly uses them to log in to the target company’s VPN platform in real-time.




























Let's personalize your content