Critical flaw in Ninja Forms WordPress Plugin actively exploited in the wild
Security Affairs
JUNE 19, 2022
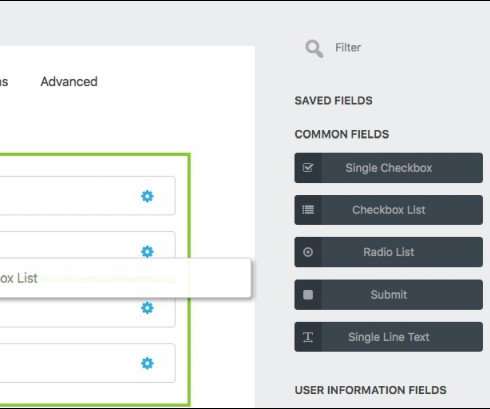
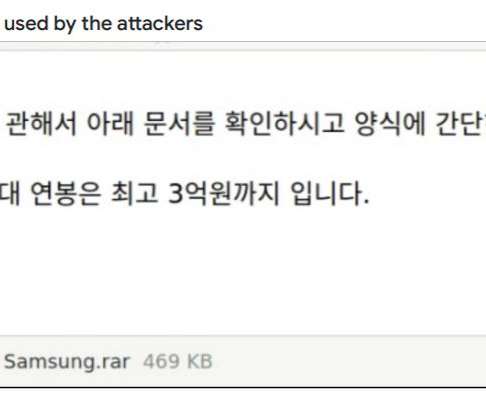
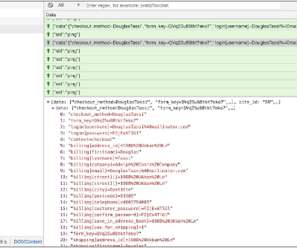
The analysis of the updates revealed that they patched a code injection vulnerability that an unauthenticated attacker can exploit to execute arbitrary code or delete arbitrary files on the websites where a separate POP chain was present. The vulnerability resides in the Merge Tag feature of the plugin. ” added the researchers.











































Let's personalize your content