YouTube creators’ accounts hijacked with cookie-stealing malware
Security Affairs
OCTOBER 20, 2021
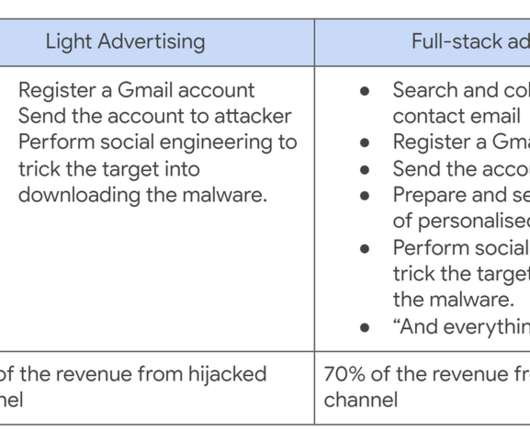
A Cookie Theft malware was employed in phishing attacks against YouTube creators, Google’s Threat Analysis Group (TAG) warns. According to Google’s Threat Analysis Group (TAG) researchers, who spotted the campaign, the attacks were launched by multiple hack-for-hire actors recruited on Russian-speaking forums.











































Let's personalize your content