Short Guide to RFID Tag Read Range — Eight FAQs
HID Global
SEPTEMBER 7, 2022
HID presents eight FAQ's regarding RFID Tag Read Range and which to consider when selecting a new tag for business process and performance.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 tag reading
tag reading 
HID Global
SEPTEMBER 7, 2022
HID presents eight FAQ's regarding RFID Tag Read Range and which to consider when selecting a new tag for business process and performance.
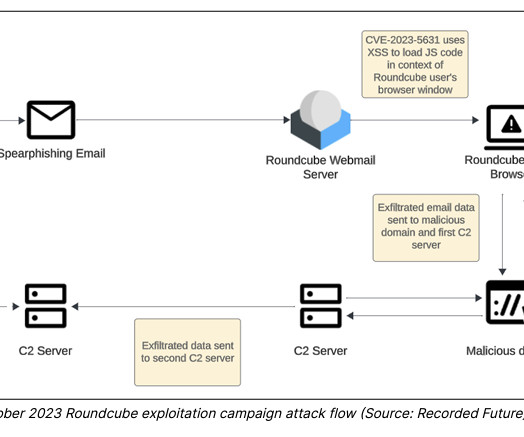
Security Affairs
FEBRUARY 19, 2024
An APT group, tracked as TAG-70, linked to Belarus and Russia exploited XSS flaws in Roundcube webmail servers to target over 80 organizations. Researchers from Recorded Future’s Insikt Group identified a cyberespionage campaign carried out by an APT group, tracked as TAG-70, linked to Belarus and Russia.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 6, 2024
Google’s TAG revealed that Commercial spyware vendors (CSV) were behind most of the zero-day vulnerabilities discovered in 2023. Google’s TAG tracked the activity of around 40 CSVs focusing on the types of software they develop. ” reads the report published by Google. ” concludes Google.
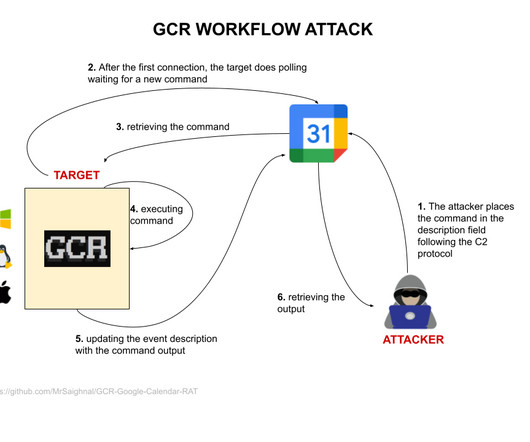
Security Affairs
NOVEMBER 6, 2023
” reads the description of the PoC published on GitHub. ” reads the Google Report. ” Google TAG has previously observed threat actors abusing Google services in their operations. At the time, TAG experts disabled the attacker-controlled Gmail accounts used as C2 infrastructure.

Security Affairs
FEBRUARY 7, 2024
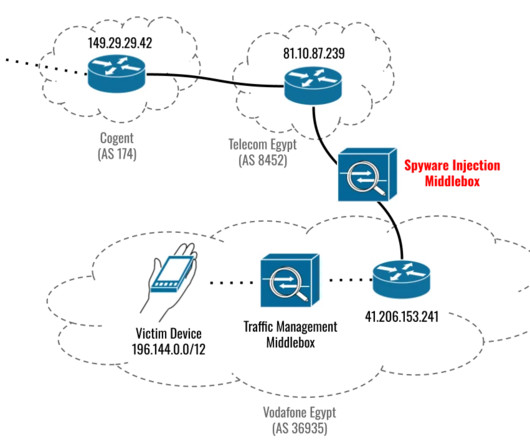
In September 2023, Citizen Lab and Google’s TAG revealed that the three recently patched Apple zero-days (CVE-2023-41993, CVE-2023-41991, CVE-2023-41992) were used to install Cytrox Predator spyware. TAG observed these exploits delivered in two different ways: the MITM injection and via one-time links sent directly to the target.
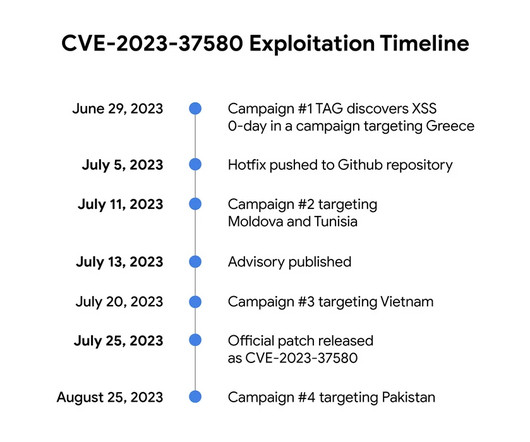
Security Affairs
NOVEMBER 16, 2023
Google TAG revealed that threat actors exploited a Zimbra Collaboration Suite zero-day ( CVE-2023-37580 ) to steal emails from governments. Google TAG researcher Clément Lecigne discovered the zero-day in June while investigating targeted attacks against Zimbra’s email server. ” reads the advisory published by Google TAG.
Security Affairs
SEPTEMBER 8, 2023
The attacks that took place in the past weeks were detected by researchers at Google’s Threat Analysis Group (TAG). “Recently, TAG became aware of a new campaign likely from the same actors based on similarities with the previous campaign. ” reads the advisory published by Google TAG.
Security Affairs
MARCH 28, 2024
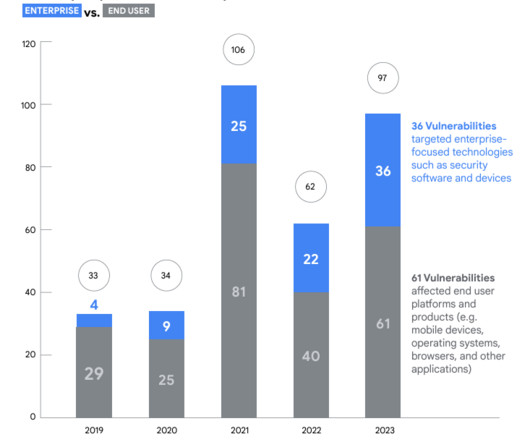
Google’s Threat Analysis Group (TAG) and Mandiant reported a surge in the number of actively exploited zero-day vulnerabilities in 2023. In 2023, Google (TAG) and Mandiant discovered 29 out of 97 vulnerabilities exploited in the wild. ” reads the report published by Google TAG.
Security Affairs
SEPTEMBER 22, 2023
Citizen Lab and Google’s TAG revealed that the three recently patched Apple zero-days were used to install Cytrox Predator spyware. reads the advisory published by the company. ” reads the report published by Citizen Lab. TAG experts explained that they were unable to capture the full Predator implant.

Security Affairs
JULY 27, 2023
It was developed by Zimbra, Inc The vulnerability is reflected Cross-Site Scripting (XSS) that was discovered by Clément Lecigne of Google Threat Analysis Group (TAG). Google TAG researchers focus on identifying and countering advanced and persistent threats. ” reads the CISA’s announcement.
Security Affairs
AUGUST 31, 2023
” reads a report published by Avinoam. The researchers ran the current process inside a fabricated container and used a mini-filter to handle their I/O requests such that it can create, read, write, and delete files on the file system using kernel primitives and avoiding security product detection. ” continues the report.

OpenText Information Management
FEBRUARY 8, 2024
Accessible PDFs are easy to use – enabling most people to view, read or interact with them. The goal is to create an inclusive experience where all PDFs and documents are crafted with accessibility in mind or appropriate tags are added for those who require such features.

Krebs on Security
APRIL 15, 2024
Image: Camdenliving.com Also, the fobs pass the credentials to his front door over the air in plain text, meaning someone could clone the fob just by bumping against him with a smartphone app made to read and write NFC tags. Neither August nor Chirp Systems responded to requests for comment.
Security Affairs
AUGUST 2, 2023
The exposure of database credentials is dangerous, as a malicious actor could use them to connect to the database and read or modify data stored within. Another piece of sensitive information that the research team observed included a Google Tag Manager ID. Then they’d be able to execute arbitrary JavaScript code on the website.
Security Affairs
JUNE 19, 2022
The vulnerability resides in the Merge Tag feature of the plugin. “One feature of Ninja Forms is the ability to add “Merge Tags” to forms that will auto-populate values from other areas of WordPress like Post IDs and logged in user’s names. ” reads the advisory published by Wordfence.

Security Affairs
NOVEMBER 30, 2022
Google’s Threat Analysis Group (TAG) linked three exploitation frameworks to a Spanish surveillance spyware vendor named Variston. While tracking the activities of commercial spyware vendors, Threat Analysis Group (TAG) spotted an exploitation framework likely linked Variston IT, a Spanish firm. ” TAG concludes.

Security Affairs
APRIL 13, 2022
The remote code execution flaw, tracked as CVE-2020-17530, resides in forced OGNL evaluation when evaluated on raw user input in tag attributes. Forced OGNL evaluation, when evaluated on raw user input in tag attributes, may lead to remote code execution – similar to S2-059.” ” reads the advisory published by Apache.
Security Affairs
DECEMBER 8, 2022
” reads the post published by TAG. TAG determined that the APT group abused the zero-day vulnerability in the JScript engine of Internet Explorer. TAG also identified other documents that were used to exploit the same vulnerability, the experts speculate they may be part of the same campaign. CVE-2017-0199 ).

Security Affairs
JULY 13, 2023
” reads the advisory published by the company. ” The vulnerability is reflected Cross-Site Scripting (XSS) that was discovered by Clément Lecigne of Google Threat Analysis Group (TAG). .” Google TAG researchers focus on identifying and countering advanced and persistent threats.
Security Affairs
MARCH 29, 2023
Google’s Threat Analysis Group (TAG) discovered several exploit chains targeting Android, iOS, and Chrome to install commercial spyware. Google’s Threat Analysis Group (TAG) shared details about two distinct campaigns which used several zero-day exploits against Android, iOS and Chrome. links sent over SMS to users.
Security Affairs
SEPTEMBER 26, 2021
Researchers from Google’s TAG team reported that financially motivated actors are using new code signing tricks to evade detection. “In these new samples, the signature was edited such that an End of Content (EOC) marker replaced a NULL tag for the ‘parameters’ element of the SignatureAlgorithm signing the leaf X.509

Security Affairs
JUNE 24, 2022
Google’s Threat Analysis Group (TAG) revealed that the Italian spyware vendor RCS Labs was supported by ISPs to spy on users. TAG researchers tracked more than 30 vendors selling exploits or surveillance capabilities to nation-state actors. ” reads the report published by Google. ” continues the analysis.

Security Affairs
APRIL 20, 2023
The researchers from Google TAG are warning of Russia-linked threat actors targeting Ukraine with phishing campaigns. Russia-linked threat actors launched large-volume phishing campaigns against hundreds of users in Ukraine to gather intelligence and aimed at spreading disinformation, states Google’s Threat Analysis Group (TAG).
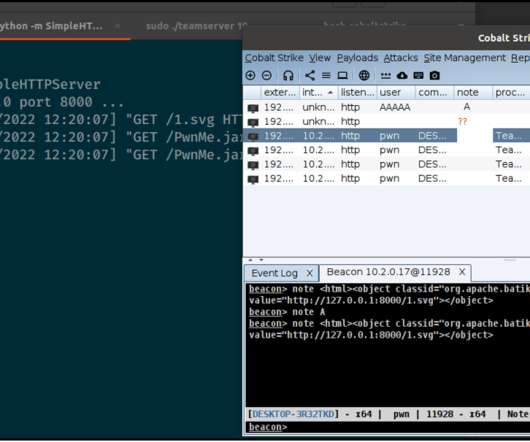
Security Affairs
OCTOBER 18, 2022
This can be exploited using an object tag, which in turn can load a malicious payload from a webserver, which is then executed by the Cobalt Strike client.” ” reads the post published by HelpSystems. “Disabling automatic parsing of html tags across the entire client was enough to mitigate this behaviour.”
Security Affairs
JULY 23, 2023
reads the report published by Citrix. reads the advisory published by CISA. “In Update on CVE-2023-3519 vulnerable IPs: we now tag 15K Citrix IPs as vulnerable to CVE-2023-3519. We extended the tagging logic to tag as vulnerable all that return Last Modified headers with a date before July 1, 2023 00:00:00Z.

Security Affairs
SEPTEMBER 8, 2022
Researchers from Google’s Threat Analysis Group (TAG) reported that some former members of the Conti cybercrime group were involved in five different campaigns targeting Ukraine between April and August 2022. ” reads the TAG’s report. ” concludes TAG.

eSecurity Planet
JUNE 1, 2023
To avoid issues, we need to understand the DMARC record tags in detail. DMARC Record Tags in Detail To understand the DMARC record, we start with an example record and then explore the detailed options for each tag. Tags are separated by semicolons ( ; ) with no extra spaces. Definitions, Pros, Cons, and More first.

Security Affairs
NOVEMBER 30, 2023
The first vulnerability, tracked as CVE-2023-42916, is an out-of-bounds read. ” reads the advisory. The fact that the issues were discovered by Google TAG suggests they were exploited by a nation-state actor or by a surveillance firm. The company addressed the flaw with improved input validation.

Security Affairs
NOVEMBER 12, 2021
Google TAG researchers discovered that threat actors leveraged a zero-day vulnerability in macOS in a watering hole campaign aimed at delivering malware to users in Hong Kong. “To protect our users, TAG routinely hunts for 0-day vulnerabilities exploited in-the-wild. ” reads the analysis published by Google.
Security Affairs
OCTOBER 20, 2021
A Cookie Theft malware was employed in phishing attacks against YouTube creators, Google’s Threat Analysis Group (TAG) warns. According to Google’s Threat Analysis Group (TAG) researchers, who spotted the campaign, the attacks were launched by multiple hack-for-hire actors recruited on Russian-speaking forums. .

Security Affairs
MARCH 31, 2022
The Google TAG uses uncovered phishing attacks targeting Eastern European and NATO countries, including Ukraine. “ However, for the first time, TAG has observed COLDRIVER campaigns targeting the military of multiple Eastern European countries, as well as a NATO Centre of Excellence.” In one case observed by the TAG team.

Gimmal
MARCH 11, 2022
Created to facilitate detection of RFID tags that are in range of the network-connected RFID antenna. Further, RFIDConnect provides the ability to program RFID tags, allowing clients to tag new items as they are captured in the Gimmal Physical software. Gimmal announces the release of the new RFIDConnect.
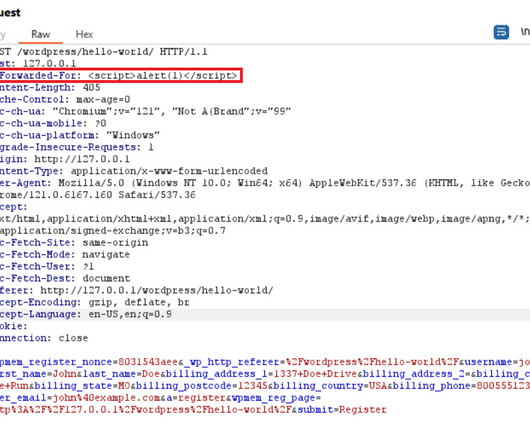
Security Affairs
APRIL 2, 2024
” reads the advisory published by Wordfence. Then the attacker can modify the raw request to contain an X-Forwarded-For header set to a malicious payload enclosed in script tags. The WP-Members Membership Plugin is currently installed on over 60,000 WordPress websites.
Security Affairs
DECEMBER 1, 2019
Google’s Threat Analysis Group (TAG) revealed that it has detected and blocked attacks carried out by nation-state actors on 12,000 of its users in the third quarter of this year. ” reads the report published by Google TAG.”We SecurityAffairs – Google TAG, state-sponsored hacking). Pierluigi Paganini.
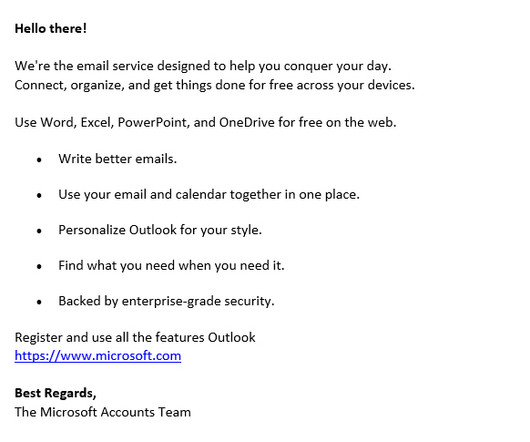
Security Affairs
OCTOBER 25, 2023
The analysis of the email HTML source code revealed the presence of a SVG tag at the end, which contains a base64-encoded payload. ” reads the analysis published by ESET. ” reads the analysis published by ESET. The messages were sent from team.managment@outlook[.]com
Security Affairs
MARCH 19, 2021
The lack of server-side validation for HTML tags in Elementor elements (i.e. “Many of these elements offer the option to set an HTML tag for the content within. tags in order to apply different heading sizes via the header_size parameter.” ” reads the post published by Wordfence.
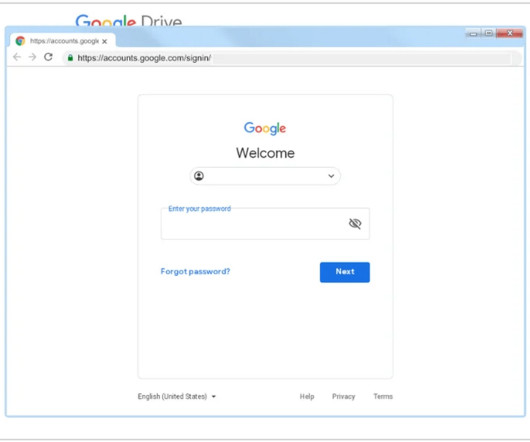
Security Affairs
APRIL 6, 2023
Google’s Threat Analysis Group (TAG) warns of a North Korea-linked cyberespionage group tracked as ARCHIPELAGO. TAG believes that the ARCHIPELAGO group is a subset of a threat actor tracked by Mandiant as APT43. ” reads the analysis published by Google TAG.
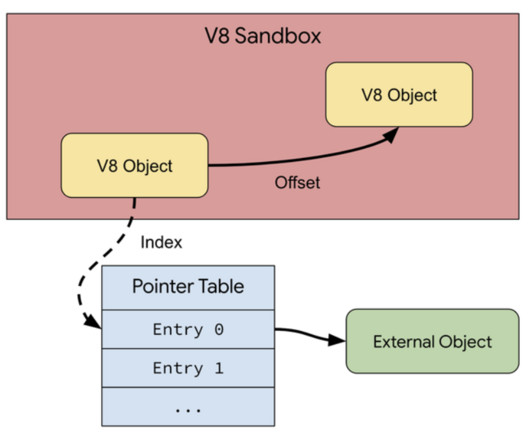
Security Affairs
APRIL 9, 2024
” reads the announcement. “In particular, neither switching to a memory safe language , such as Rust, nor using current or future hardware memory safety features, such as memory tagging , can help with the security challenges faced by V8 today.”

Security Affairs
DECEMBER 14, 2022
. “An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which rely on MOTW tagging.” ” reads the advisory published by the IT giant. ” reads the advisory.

Security Affairs
OCTOBER 4, 2023
” reads the advisory published by the company. The flaw was discovered by security researcher Clément Lecigne from Google’s Threat Analysis Group (TAG). . “A local attacker may be able to elevate their privileges. The vulnerability impacts iPhone XS and later, iPad Pro 12.9-inch
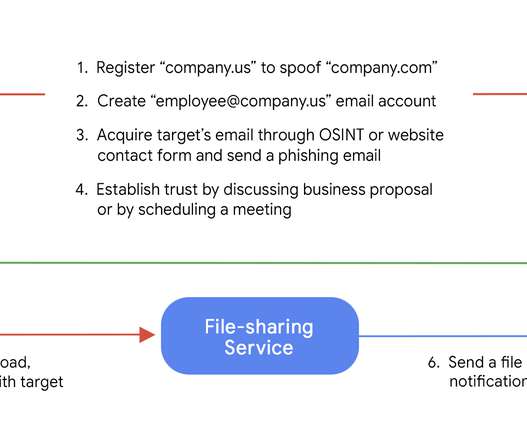
Security Affairs
MARCH 19, 2022
Google’s Threat Analysis Group (TAG) uncovered a new initial access broker, named Exotic Lily, that is closely affiliated with the Conti ransomware gang. Google’s Threat Analysis Group (TAG) researchers linked a new initial access broker, named Exotic Lily, to the Conti ransomware operation.
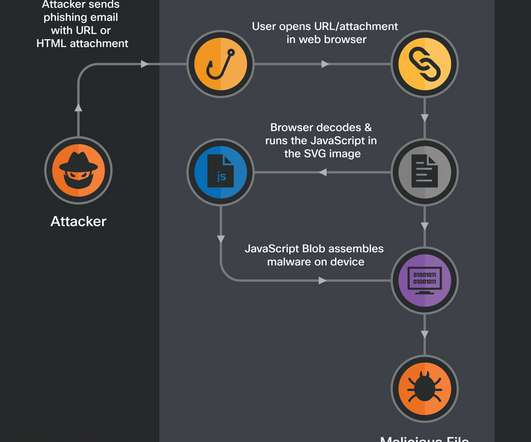
Security Affairs
DECEMBER 14, 2022
. “SVG images are constructed using XML, allowing them to be placed within HTML using ordinary XML markup tags. Talos has identified malicious emails featuring HTML attachments with encoded SVG images that themselves contain HTML <script> tags. Including script tags within a SVG image is a legitimate feature of SVG.”

Security Affairs
DECEMBER 8, 2020
The remote code execution flaw, tracked as CVE-2020-17530, resides in forced OGNL evaluation when evaluated on raw user input in tag attributes. “Forced OGNL evaluation, when evaluated on raw user input in tag attributes, may lead to remote code execution – similar to S2-059.”

Security Affairs
DECEMBER 20, 2023
Reported by Clément Lecigne and Vlad Stolyarov of Google’s Threat Analysis Group on 2023-12-19” reads the advisory published by the IT giant. ” The fact that the issue was discovered by Google TAG suggests it was exploited by a nation-state actor or by a surveillance firm.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content