Abusing Windows Container Isolation Framework to avoid detection by security products
Security Affairs
AUGUST 31, 2023
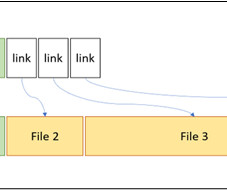
Algorithms based on this log source look for certain patterns to detect file system-based malware and prevent them before any irreversible damage is done. For example, a process that opens many existing files and writes to them will be classified as ransomware/wiper, depending on the data written.” ” continues the report.












































Let's personalize your content