Google announces V8 Sandbox to protect Chrome users
Security Affairs
APRIL 9, 2024
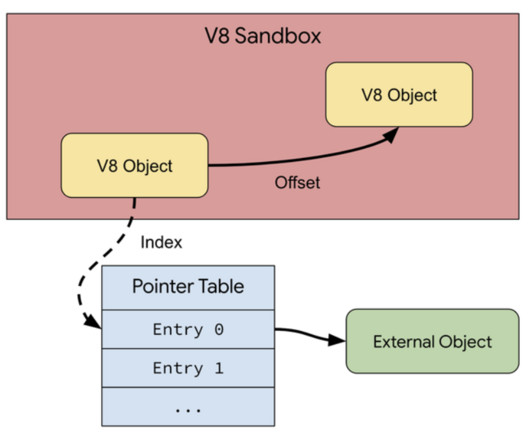
“In particular, neither switching to a memory safe language , such as Rust, nor using current or future hardware memory safety features, such as memory tagging , can help with the security challenges faced by V8 today.” As such, existing memory safety solutions are, for the most part, not applicable to V8.”













































Let's personalize your content