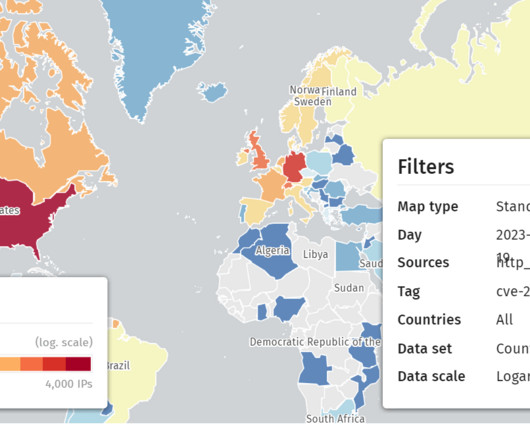
Shadowserver reported that +15K Citrix servers are likely vulnerable to attacks exploiting the flaw CVE-2023-3519
Security Affairs
JULY 23, 2023
Most of the servers are located in the United States and Germany. Update on CVE-2023-3519 vulnerable IPs: we now tag 15K Citrix IPs as vulnerable to CVE-2023-3519. We extended the tagging logic to tag as vulnerable all that return Last Modified headers with a date before July 1, 2023 00:00:00Z.




























Let's personalize your content