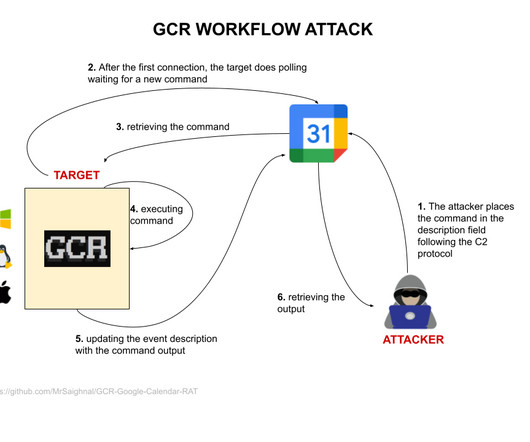
Attackers use Google Calendar RAT to abuse Calendar service as C2 infrastructure
Security Affairs
NOVEMBER 6, 2023
The target will connect directly to Google.” ” Google TAG has previously observed threat actors abusing Google services in their operations. In March 2023, TAG spotted an Iran-linked APT group using macro docs to infect users with a small.NET backdoor, BANANAMAIL that relies on Gmail as C2 infrastructure.











































Let's personalize your content