This tiny, tamper-proof ID tag can authenticate almost anything via MIT News
IG Guru
FEBRUARY 21, 2024
The post This tiny, tamper-proof ID tag can authenticate almost anything via MIT News first appeared on IG GURU. Check out the article here.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 tag
tag  Authentication Related Topics
Authentication Related Topics 
IG Guru
FEBRUARY 21, 2024
The post This tiny, tamper-proof ID tag can authenticate almost anything via MIT News first appeared on IG GURU. Check out the article here.

Security Affairs
JULY 13, 2023
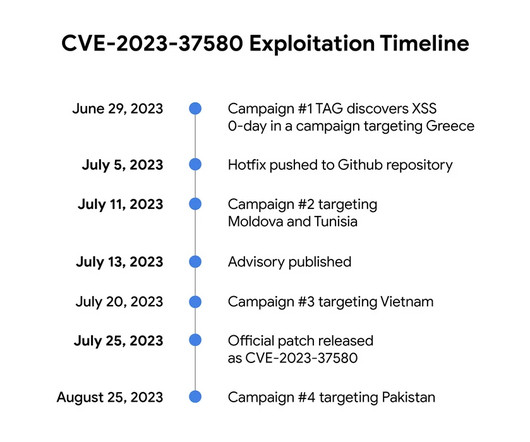
.” The vulnerability is reflected Cross-Site Scripting (XSS) that was discovered by Clément Lecigne of Google Threat Analysis Group (TAG). Google TAG researchers focus on identifying and countering advanced and persistent threats. Thank you to @Zimbra for publishing this advisory and mitigation advice!
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
NOVEMBER 16, 2023
Google TAG revealed that threat actors exploited a Zimbra Collaboration Suite zero-day ( CVE-2023-37580 ) to steal emails from governments. Google TAG researcher Clément Lecigne discovered the zero-day in June while investigating targeted attacks against Zimbra’s email server. ” reads the advisory published by Google TAG.

Schneier on Security
NOVEMBER 21, 2023
TAG has observed four different groups exploiting the same bug to steal email data, user credentials, and authentication tokens. To ensure protection against these types of exploits, TAG urges users and organizations to keep software fully up-to-date and apply security updates as soon as they become available.

Security Affairs
JULY 29, 2019
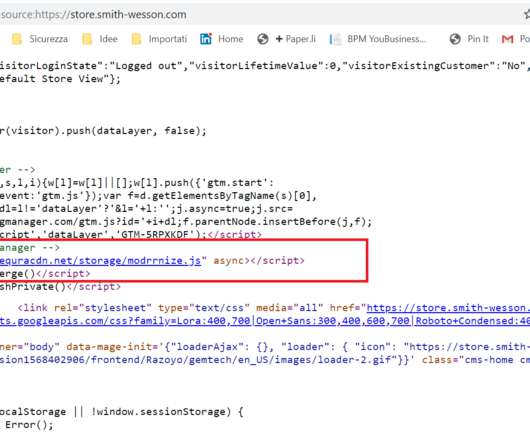
Security experts at Plugin Vulnerabilities have discovered an authenticated Persistent Cross-Site Scripting (XSS) flaw in Facebook Widget. Researchers at Plugin Vulnerabilities have discovered an authenticated Persistent Cross-Site Scripting (XSS) flaw in the Facebook Widget (Widget for Facebook Page Feeds). Pierluigi Paganini.
Security Affairs
DECEMBER 3, 2019
The vulnerability affects the way Microsoft applications use OAuth for authentication, these applications trust certain third-party domains and sub-domains that are not registered by Microsoft. An attacker could embed an iframe tag into a website with the “src” attribute set to the crafted link, then trick the victim into visiting it.

OpenText Information Management
APRIL 19, 2024
VIPER: Well, if IoT was an emoji or an expression, it would be: (1) a cloud with legs, (2) a tornado of devices, or (3) an air-tag tracking anything (keys, dog, purse, avocado). From QR codes to RFID tags to Bluetooth devices, the ability to track and trace physical assets has become much easier. You: What is IoT?

The Last Watchdog
AUGUST 8, 2023
DigiCert Trust Lifecycle Manager additionally supports enrollment to a broad range of Microsoft and AWS technologies, providing organizations a unified approach to managing public and private trust for use cases such as biometric authentication, device authentication, WiFi/VPN provisioning, cloud workloads and infrastructure management.
Security Affairs
MARCH 19, 2021
The lack of server-side validation for HTML tags in Elementor elements (i.e. “Many of these elements offer the option to set an HTML tag for the content within. tags in order to apply different heading sizes via the header_size parameter.” tags in order to apply different heading sizes via the header_size parameter.”

eSecurity Planet
JUNE 1, 2023
At a high level, implementation of the Domain-based Message Authentication, Reporting and Conformance (DMARC) standard can be done simply and easily for outgoing mail by adding a text file to an organization’s DNS record. To avoid issues, we need to understand the DMARC record tags in detail.
Security Affairs
OCTOBER 20, 2021
A Cookie Theft malware was employed in phishing attacks against YouTube creators, Google’s Threat Analysis Group (TAG) warns. According to Google’s Threat Analysis Group (TAG) researchers, who spotted the campaign, the attacks were launched by multiple hack-for-hire actors recruited on Russian-speaking forums. .
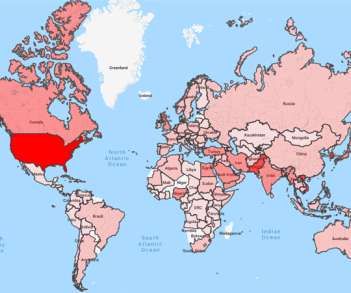
Security Affairs
DECEMBER 1, 2019
Google’s Threat Analysis Group (TAG) revealed that it has detected and blocked attacks carried out by nation-state actors on 12,000 of its users in the third quarter of this year. ” reads the report published by Google TAG.”We SecurityAffairs – Google TAG, state-sponsored hacking). Pierluigi Paganini.
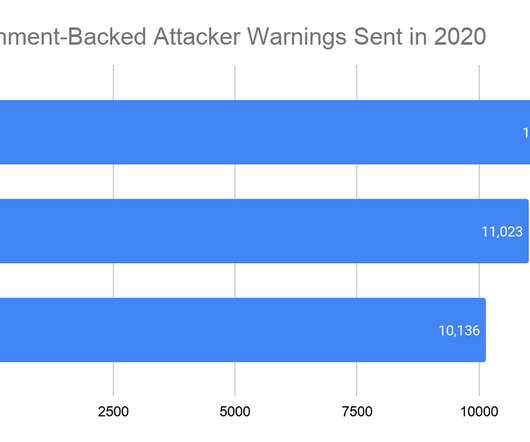
Security Affairs
OCTOBER 17, 2020
Shane Huntley, Director at Google’s Threat Analysis Group (TAG), revealed that her team has shared its findings with the campaigns and the Federal Bureau of Investigation. ” reads the report published by Google TAG. SecurityAffairs – hacking, Google TAG). Pierluigi Paganini.

Security Affairs
FEBRUARY 25, 2024
Iran Crisis Russia-Aligned TAG-70 Targets European Government and Military Mail Servers in New Espionage Campaign U.S.

Security Affairs
FEBRUARY 5, 2024
An authenticated attacker can exploit the issue to access certain restricted resources. The flaw CVE-2024-21893 is a server-side request forgery vulnerability in the SAML component of Connect Secure (9.x, x), Policy Secure (9.x, x) and Neurons for ZTA.
Krebs on Security
AUGUST 9, 2022
Microsoft this month also issued a different patch for another MSDT flaw, tagged as CVE-2022-35743. ” Greg Wiseman , product manager at Rapid7 , pointed to an interesting bug Microsoft patched in Windows Hello , the biometric authentication mechanism for Windows 10.
eSecurity Planet
MARCH 16, 2023
. “An attacker who successfully exploited this vulnerability could access a user’s Net-NTLMv2 hash which could be used as a basis of an NTLM Relay attack against another service to authenticate as the user,” the company wrote. This will prevent the sending of NTLM authentication messages to remote file shares.

Security Affairs
MARCH 14, 2023
The CVE-2023-23397 flaw is a Microsoft Outlook spoofing vulnerability that can lead to an authentication bypass. “An attacker who successfully exploited this vulnerability could access a user’s Net-NTLMv2 hash which could be used as a basis of an NTLM Relay attack against another service to authenticate as the user.”

Security Affairs
MAY 28, 2022
According to Reuters, at least victims of the leak confirmed the authenticity of the messages and revealed they were targeted by Russia-linked hackers. ” reported the Reuters. “Dearlove said that the emails captured a “legitimate lobbying exercise which, seen through this antagonistic optic, is now subject to distortion.””

The Last Watchdog
NOVEMBER 19, 2018
A string of advances in biometric authentication systems has brought facial recognition systems, in particular, to the brink of wide commercial use. Many of these photos are tagged with the identity of the people in them. Related: Drivers behind facial recognition boom. Cameras have become cheap and ubiquitous.

Security Affairs
APRIL 8, 2023
The CVE-2023-26083 flaw in the Arm Mali GPU driver is chained with other issues to install commercial spyware, as reported by Google’s Threat Analysis Group (TAG) in a recent report. Mandiant researchers first observed this affiliate targeting Veritas issues in the wild on October 22, 2022.
Security Affairs
JANUARY 25, 2022
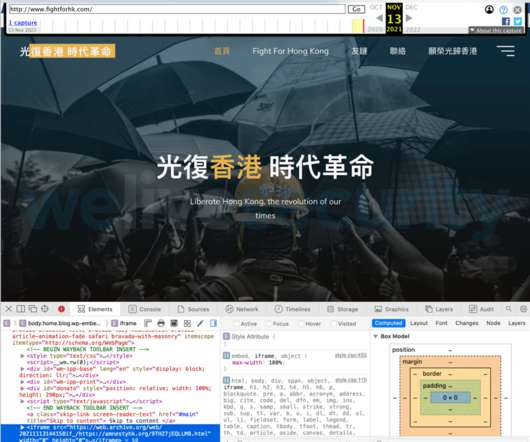
The investigation started in November after Google TAG published a blogpost about watering-hole attacks targeting macOS users in Hong Kong. Google TAG researchers discovered that threat actors leveraged a zero-day vulnerability in macOS in a watering hole campaign aimed at delivering malware to users in Hong Kong.
Security Affairs
JANUARY 18, 2021
While conducting reconnaissance and fingerprinting the experts found three Apple hosts running a content management system (CMS) backed by Lucee , which is a dynamic, Java-based, tag and scripting language used for rapid web application development. The three hosts are: [link] (Recent version) [link] (Older version) [link] (Older version).

Krebs on Security
DECEMBER 14, 2022
The vulnerability allows attackers to craft documents that won’t get tagged with Microsoft’s “Mark of the Web,” despite being downloaded from untrusted sites. “What actions are required is not clear; however, we do know that exploitation requires an authenticated user level of access,” Breen said.

Security Affairs
JULY 4, 2019
In this way, he can hijack the session from a user and then exploit an authenticated Remote Code Execution (RCE) flaw to completely takeover the online store. “An authenticated Remote Code Execution vulnerability is then exploited, which results in a full takeover of the store by the attacker. ” continues the post.

Security Affairs
SEPTEMBER 2, 2021
The flaw is an OGNL injection issue that can be exploited by an authenticated attacker to execute arbitrary code on affected Confluence Server and Data Center instances. “An Query our API for "tags=CVE-2021-26084" for full payload and source IPs. reads the advisory published by the company.

eSecurity Planet
DECEMBER 14, 2022
Regarding that flaw, Microsoft observed, “An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which rely on MOTW tagging.”
Security Affairs
MAY 14, 2020
Search Console, Analytics, Tag Manager, PageSpeed Insights, Optimize, and AdSense), giving users authoritative and up-to-date advice on how to succeed on the web, it has over 300,000 active installations. ” reads the analysis published by Wordfence. ” reads the analysis published by Wordfence. ” continues the analysis.

Security Affairs
MARCH 9, 2020
Knowledge of a the validation key allows an authenticated user with a mailbox to pass arbitrary objects to be deserialized by the web application, which runs as SYSTEM.” A remote, authenticated attacker could exploit the CVE-2020-0688 vulnerability to execute arbitrary code with SYSTEM privileges on a server and take full control.

eSecurity Planet
MARCH 1, 2023
To prevent unwanted access and protect data in transit, wireless connections must be secured with strong authentication procedures, encryption protocols, access control rules, intrusion detection and prevention systems, and other security measures. As a result, wireless networks are prone to eavesdropping, illegal access and theft.

eSecurity Planet
OCTOBER 17, 2023
That’s where VLAN tagging — the practice of adding metadata labels, known as VLAN IDs, to information packets on the network — can help. These informative tags help classify different types of information packets across the network, making it clear which VLAN each packet belongs to and how they should operate accordingly.

Security Affairs
FEBRUARY 12, 2024
However, with proper rotation and usage, they can offer a speedy solution for your internet endeavours without the higher price tag of their residential counterparts. Due to their nature, datacenter proxies can raise red flags for some websites, leading to a higher chance of being blocked if used recklessly.

Krebs on Security
AUGUST 19, 2020
Time is of the essence in these attacks because many companies that rely on VPNs for remote employee access also require employees to supply some type of multi-factor authentication in addition to a username and password — such as a one-time numeric code generated by a mobile app or text message.

Security Affairs
APRIL 3, 2022
Sophos Firewall affected by a critical authentication bypass flaw Mar 20- Mar 26 Ukraine – Russia the silent cyber conflict Security Affairs newsletter Round 358 by Pierluigi Paganini Western Digital addressed a critical bug in My Cloud OS 5 CISA adds 66 new flaws to the Known Exploited Vulnerabilities Catalog.

eSecurity Planet
MAY 24, 2023
The DomainKeys Identified Mail (DKIM) email authentication standard enables email servers to check incoming emails to verify the sender and detect email message alterations. Related Email Authentication Standards DKIM provides authentication of the integrity of sent emails with a narrow scope.
Security Affairs
OCTOBER 31, 2022
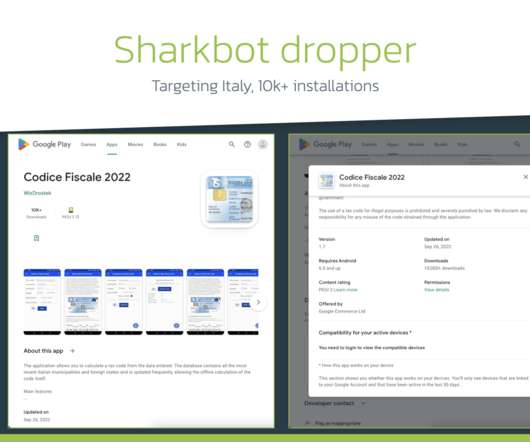
The apps masqueraded as security authenticators or file recovery tools and deliver a novel variant of Vultur Android Banking malware. “Android offers a way to tag the content of the window as secure, by using the “FLAG_SECURE” , which prevents it “from appearing in screenshots or from being viewed on non-secure displays”.

The Last Watchdog
SEPTEMBER 7, 2022
The price tag of the ransom is just one of the many costs of these attacks, and remediation can often exceed this fee many times over. Bolster your monitoring and email authentication capabilities. Sometimes ransom payments are recovered, but not always. The impact of ransomware. Incident response.

eSecurity Planet
OCTOBER 26, 2021
In any instance, cryptographic authentication of SBOMs is imperative for verifying their authenticity. SWID: Software Identification Tagging. Towards the end of the 2010s, the International Organizations for Standards (ISO) began developing a standard for tagging software components with machine-readable IDs.

Security Affairs
APRIL 12, 2019
According to security experts at WordFence, the vulnerability in Yuzo plugin stems from missing authentication checks in the plugin routines used to store settings in the database. “The vulnerability in Yuzo Related Posts stems from missing authentication checks in the plugin routines responsible for storing settings in the database.”

Collibra
JANUARY 23, 2023
Zero trust, a government wide initiative Zero-trust was originally introduced as a network-based architecture mode, which centralized on identity and multi-factor authentication. To begin with, as the memo acknowledges, it will be challenging for many agencies to develop an accurate approach to categorizing data and tagging data.
Security Affairs
APRIL 28, 2020
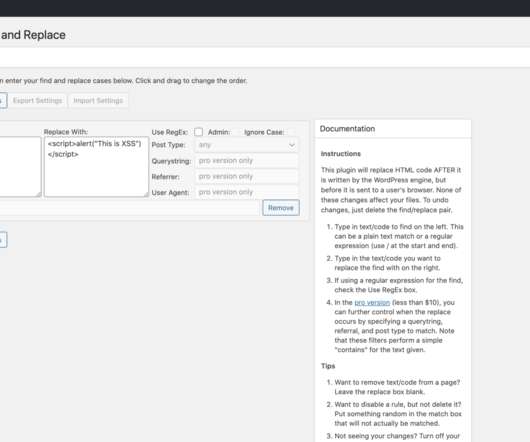
“An attacker could use this vulnerability to replace a HTML tag like with malicious Javascript. This would cause the malicious code to execute on nearly every page of the affected site, as nearly all pages start with a HTML tag for the page header, creating a significant impact if successfully exploited.”

Security Affairs
AUGUST 6, 2023
Pro-Russian hackers claim attacks on Italian banks Hacktivists fund their operations using common cybercrime tactics Bitfinex Hacker and Wife Plead Guilty to Money Laundering Conspiracy Involving Billions in Cryptocurrency A cyberattack has disrupted hospitals and health care in several states FBI warns of scammers posing as NFT devs to steal your (..)

OneHub
DECEMBER 14, 2020
That’s a devastating price tag for many companies. Two-factor authentication keeps your files secure even if your passwords are compromised. Two-factor authentication (2FA) is a quick additional login step that ups the security of your accounts. This code can be obtained either by an authenticator app or via text message.

Security Affairs
JULY 18, 2020
RECON is caused by the lack of authentication in an SAP NetWeaver AS for Java web component. Query our API for "tags=CVE-2020-6287" for a full list of source IP addresses and relevant indicators. Mass scanning activity started around 2020-07-15T17:48:37Z. threatintel [link] — Bad Packets (@bad_packets) July 16, 2020.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content