Abusing Windows Container Isolation Framework to avoid detection by security products
Security Affairs
AUGUST 31, 2023
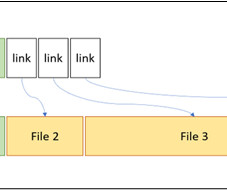
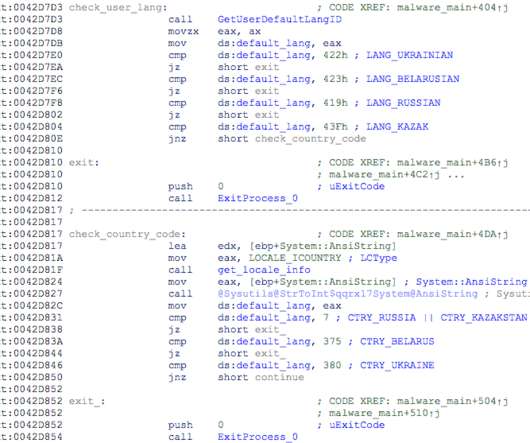
Algorithms based on this log source look for certain patterns to detect file system-based malware and prevent them before any irreversible damage is done. ” The researchers published examples of simple wiping and ransomware algorithms using the driver. ” continues the report. ” continues the report.













































Let's personalize your content