RSAC Fireside Chat: StackHawk helps move the application security needle to ‘shift everywhere’
The Last Watchdog
APRIL 20, 2023
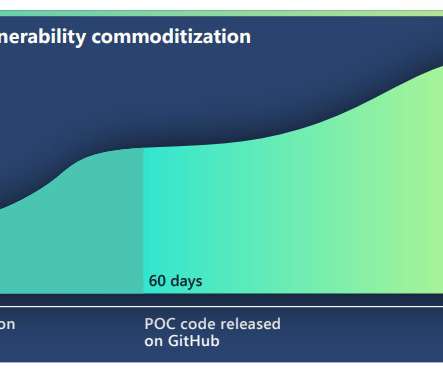
Embedding security into the highly dynamic way new software gets created and put into service — on the fly, by leveraging ephemeral APIs — has proven to be a daunting challenge. This has led to security vendors, StackHawk among them, putting great energy into weaving security more tightly into DevOps, CICD and more.




































Let's personalize your content