GoDaddy Employees Used in Attacks on Multiple Cryptocurrency Services
Krebs on Security
NOVEMBER 21, 2020
The attacks were facilitated by scams targeting employees at GoDaddy , the world’s largest domain name registrar, KrebsOnSecurity has learned. The incident is the latest incursion at GoDaddy that relied on tricking employees into transferring ownership and/or control over targeted domains to fraudsters. and 11:00 p.m. PST on Nov.



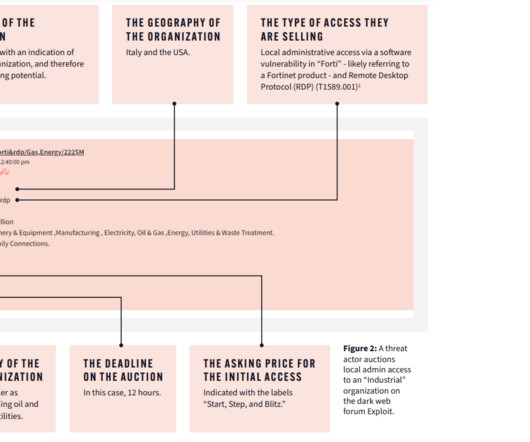






























Let's personalize your content