Accelerate release lifecycle with pathway to deploy: Part 2
IBM Big Data Hub
DECEMBER 19, 2023
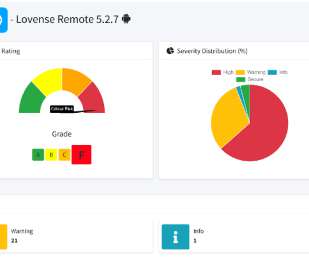
Stage 1: Development automation Infrastructure automation (IaC) and pipeline automation are self-contained within the development team, which makes automation a great place to start. Overall Cloud Capability Centre (CCC), or the equivalent core team, plays a significant role in driving change with application and platform teams.




































Let's personalize your content