Facebook Trains Its AI on Your Data. Opting Out May Be Futile
WIRED Threat Level
SEPTEMBER 7, 2023
Here's how to request that your personal information not be used to train Meta's AI model. ";Request" is the operative word here.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 request-quote
request-quote 
WIRED Threat Level
SEPTEMBER 7, 2023
Here's how to request that your personal information not be used to train Meta's AI model. ";Request" is the operative word here.

Thales Cloud Protection & Licensing
APRIL 22, 2024
This is significant because advanced bot traffic poses a substantial risk even at low volumes, as advanced bad bots can achieve their goals with fewer requests than simpler bad bots and are much more persistent in staying on their designated target. of the sector's bad bot traffic comes from advanced bots, compared to gaming's 45.9%.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
MARCH 20, 2024
Gaskell has been quoted in multiple “articles” about random subjects, such as this article at HRDailyAdvisor about the pros and cons of joining a company-led fantasy football team. Also quoted in this article is Sally Stevens , who is cited as HR Manager at FastPeopleSearch[.]io. Requests for comment were sent to H.I.G.

Krebs on Security
MAY 22, 2023
“This was three hours non-stop, 200,000 to 400,000 requests per second,” Chaput said of the DDoS. ” Chaput said a review of their logs indicates many of the newly registered Mastodon spam accounts were registered using the same 0auth credentials, and that a domain common to those credentials was quot[.]pw.

KnowBe4
JANUARY 12, 2023
Levinson quotes Rita Reynolds, Chief Information Officer for the National Association of Counties, as saying that customer-facing county employees might be more likely to assume that requests are legitimate, since they deal with so many people each day. Attackers use different tactics to target government employees in specific roles.
Enterprise Software Blog
MARCH 28, 2023
";Jwt": { "Issuer": "[link] "Audience": "[link] "Key": "S1u*p7e_r+S2e/c4r6e7t*0K/e7y" } Once the token configurations have been defined, we can configure the JWT service in the Program.cs

Krebs on Security
FEBRUARY 9, 2024
” The company has not yet responded to requests for information about exactly when those overly permissive user rights were introduced. ET: An earlier version of this story quoted George as saying he was able to see support information for the U.S. Update, 11:01 a.m. Department of Defense.

Security Affairs
OCTOBER 17, 2022
. “”Here, not only the website of the presidency is under attack, the object of the attack is the entire Bulgarian state as part of the European family,” said Ivan Geshev, quoted by BTA. They would request his extradition, but the Russian government will never provide support to the request of the Bulgarian authorities.

Hunton Privacy
FEBRUARY 22, 2021
The NYDFS learned of the threat after receiving reports from auto insurers that cybercriminals were targeting their premium quote sites to steal driver’s license numbers. Blocking the IP addresses of suspected unauthorized users and considering quote limits per user session.
Krebs on Security
NOVEMBER 4, 2021
com — from a desktop web browser redirects the visitor to a harmless page with ads for car insurance quotes. Clicking “Schedule new delivery” brings up a page that requests your name, address, phone number and date of birth. .” Attempting to visit the domain in the phishing link — o001cfedeex[.]com
Security Affairs
AUGUST 11, 2020
The vulnerability was discovered by the researcher Jeffrey Hofmann from Praetorian, it resides in the way TeamViewer quotes its custom URI handlers. The expert discovered that the issue could allow an attacker to force the software to relay an NTLM authentication request to the attacker’s system. for the Windows platform.

Krebs on Security
MARCH 16, 2021
An expert on SIM-swapping attacks who’s been quoted quite a bit on this blog , Nixon said she also had Lucky225 test his interception tricks on her mobile phone, only to watch her incoming SMS messages show up on his burner phone. Allison Nixon is chief research officer at Unit221B , a New York City-based cyber investigations firm.

IBM Big Data Hub
FEBRUARY 28, 2024
They handle upstream sourcing activities like contract negotiation, sending requests for proposals (RFPs) and requests for quotes (RFQs) as well as managing the supplier relationship once selected. However, due to their symbiosis, sourcing and procurement strategies often share similar initiatives, business goals and metrics.
Security Affairs
OCTOBER 1, 2022
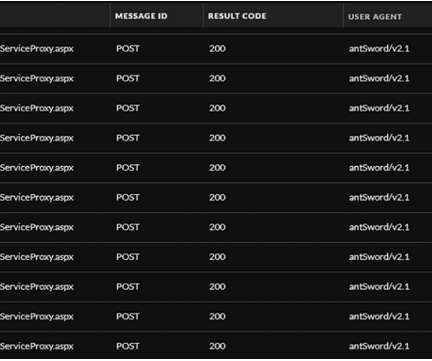
The first flaw, tracked as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) issue. GTSC recommends adding a rule to block requests with indicators of attacks through the URL Rewrite Rule module on IIS server. Select Request Blocking and click OK. Powershell.*” (excluding quotes) and click OK. Select Autodiscover.

Security Affairs
MARCH 12, 2024
After the first contact via instant messaging channels, further documents are then requested and a quote is provided.

eSecurity Planet
APRIL 14, 2023
Pricing Radware doesn’t display its pricing; you can request a quote through their contact page. Pricing Cloudflare doesn’t display its pricing; you can request a quote based on what you need through their pricing page. Limited customization options for smaller businesses.
Security Affairs
MARCH 12, 2022
In these initial contact form submissions, the attacker posed as an employee at a Canadian luxury construction company looking for a quote for a product provided by the target.” . “Rather than directly sending a phishing email, the attacker in these cases initiated a conversation through an organization’s website contact form.

Security Affairs
OCTOBER 4, 2022
The first flaw, tracked as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) issue. Select Request Blocking and click OK. Powershell.*” (excluding quotes) and click OK. The second vulnerability, tracked as CVE-2022-41082, allows remote code execution (RCE) when PowerShell is accessible to the attacker. Select Autodiscover.

eSecurity Planet
FEBRUARY 21, 2024
Your teams should also know who’s responsible for the request and upkeep of each rule. Additionally, confirm whether the owners of that process have shared any relevant documentation with new team members, and ensure that everyone knows how to submit a change request or access the documentation.

eSecurity Planet
OCTOBER 1, 2022
A day after GTSC published its blog post, Microsoft released customer guidance on how to mitigate the vulnerabilities, which affect Microsoft Exchange Server 2013, 2016 and 2019, and are identified as the Server-Side Request Forgery (SSRF) vulnerability CVE-2022-41040 and the RCE flaw CVE-2022-41082. autodiscover.json.*@.*Powershell.*

Krebs on Security
FEBRUARY 14, 2020
The IRS official who contacted me was not authorized to be quoted in the media (and indeed did not initially realize he was speaking to a member of the press when he called). Requests for this information from the Justice Department office that prosecuted the case — the U.S.

Security Affairs
JANUARY 19, 2019
A bug in Microsoft partner portal ‘exposes ‘ support requests to all partners, fortunately, no customer data was exposed. The Register in exclusive reported that Microsoft partner portal ‘exposed ‘every’ support request filed worldwide.’ Stuart Crane of IT biz Everon told The Register.

DLA Piper Privacy Matters
JUNE 4, 2020
Information requests. mediation requests). Requests for advice on draft laws, decrees and decisions. The Belgian Data Protection Authority (BDPA) used the GDPR second anniversary as a milestone to issue a news alert with statistics on the actions it has taken since May 2019 (figures from 25/05/2019 to 20/05/2020). Statistics.

Krebs on Security
JUNE 18, 2020
A follow-up story that same month examined the work of a cybercrime gang that was hacking into HR departments at healthcare organizations across the country and filing fraudulent tax refund requests with the IRS on employees of those victim firms.
eSecurity Planet
FEBRUARY 26, 2021
This information is then analyzed to determine if the client request is from a human user or a bot. . Kasada uses a unique mitigative method that scales the difficulty of accessing web applications based on a growing number of requests. You can request a demo or contact the company for a quote. Kasada plans.
Enterprise Software Blog
FEBRUARY 9, 2023
Default is " SUM " Removing aggregation for category labels will remove the aggregation for all value fields. Keep in mind there are two data access states upon App Preview. Users can individually change the aggregation function for value fields.
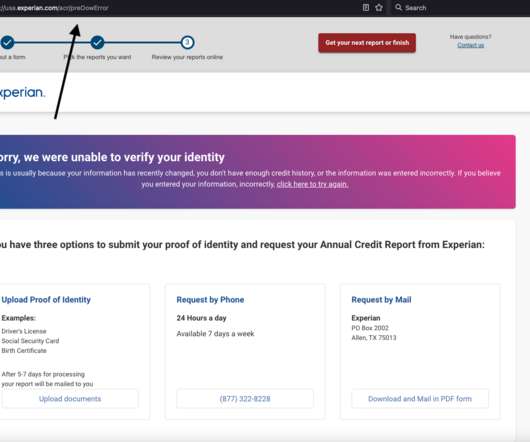
Krebs on Security
JANUARY 9, 2023
Experian said I had three options for a free credit report at this point: Mail a request along with identity documents, call a phone number for Experian, or upload proof of identity via the website. 23 notification, but the company has so far ignored multiple requests for comment or clarification. ” Sen.

IBM Big Data Hub
JANUARY 18, 2024
Chatbots can help your customers and potential clients find or input information quickly by instantly responding to requests that use audio input, text input or a combination of both, eliminating the need for human intervention or manual research. Providing fast and accurate answers helps build long-term customer relationships.
eSecurity Planet
FEBRUARY 26, 2021
This information is then analyzed to determine if the client request is from a human user or a bot. . Kasada uses a unique mitigative method that scales the difficulty of accessing web applications based on a growing number of requests. You can request a demo or contact the company for a quote. Kasada plans.

Hunton Privacy
DECEMBER 26, 2019
In March 2019, OCR received a complaint that “Korunda [had] failed to forward a patient’s medical records in electronic format to a third party” after multiple requests by the patient. Despite OCR’s assistance, Korunda continued to fail to provide the requested records, which resulted in another complaint to OCR.

Krebs on Security
MAY 3, 2019
Bessemer further alleges Fiserv’s systems had no checks in place to prevent automated attacks that might let thieves rapidly guess the last four digits of the customer’s SSN — such as limiting the number of times a user can submit a login request, or imposing a waiting period after a certain number of failed login attempts.

Krebs on Security
OCTOBER 28, 2020
Larsson quotes Gunnebo CEO Stefan Syrén saying the company never considered paying the ransom the attackers demanded in exchange for not publishing its internal documents. What’s more, Syrén seemed to downplay the severity of the exposure. ” It remains unclear whether the stolen RDP credentials were a factor in this incident.

ForAllSecure
APRIL 20, 2021
Across ForAllSecure’s community engagements, a consistent request we’ve received is for more educational material and general resources around fuzz testing. Quotes and advice from product security veterans. The goal was to help the product security industry feel connected during a time of social distancing.

ForAllSecure
APRIL 20, 2021
Across ForAllSecure’s community engagements, a consistent request we’ve received is for more educational material and general resources around fuzz testing. Quotes and advice from product security veterans. The goal was to help the product security industry feel connected during a time of social distancing.
Troy Hunt
MARCH 10, 2021
Because it's free, works well and does something genuinely useful, it's become quite popular: Now up to 909M requests to @haveibeenpwned 's Pwned Passwords in the last month. Equally, Home Assistant sends outbound requests all the time, it's how you know when there's update! How long until it hits the big "1B"? ??

Krebs on Security
NOVEMBER 20, 2019
That 2014 story declined to quote Rasbora by name because he was a minor then, but his father seemed alarmed enough about my inquiry that he insisted his son speak with me about the matter. His dad hung up on me when I called Wednesday evening requesting comment. 13, 2014. “I I also have [a] major concern what my 15 yo son [is] doing.

Krebs on Security
NOVEMBER 7, 2018
The USPS did not respond to repeated requests for comment over the past six days. One resident was quoted as saying she received a bill for $2,000 in charges on a card she’d never seen before, and only after that did she get a notice from the USPS saying someone at her address had signed up for Informed Delivery.

Armstrong Archives
MARCH 13, 2024
Contact us today for expert scanning solutions or request a free quote ! Choose an experienced partner like Armstrong Archives so that your company can enjoy a seamless transition from physical to digital documents. Ready to transform your medical records management?
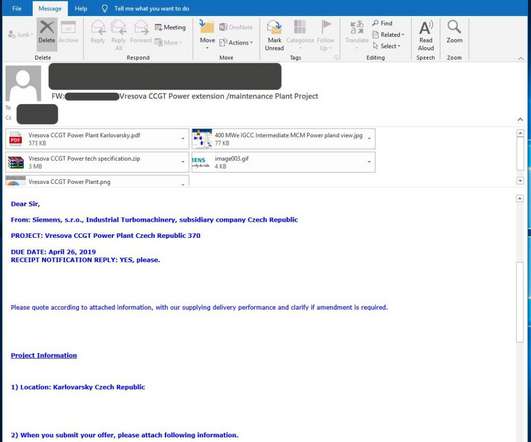
Security Affairs
DECEMBER 18, 2019
The attachments are “industrial-themed,” they include white papers, power plant diagrams, and quote requests for blueprints of facilities. Threat actors launched spear-phishing attacks using emails with malicious attachments often disguised as PDF files.

National Archives Records Express
APRIL 1, 2019
After developing requirements, agencies can issue Requests for Quotes (RFQs) or Requests for Information (RFIs) for specific ERM services and solutions on GSA eBuy. Do you have examples of Requests for Information (RFI) or Requests for Quotation (RFQ) from agencies? ERM SOLUTIONS.

Thales Cloud Protection & Licensing
DECEMBER 13, 2018
Until further notice, all quotes, orders, contracts and other agreements will remain with the current Thales legal entity you are operating with and all applicable terms and conditions remain unchanged, though those related to the nShield product line will now be managed exclusively by nCipher Security.
Enterprise Software Blog
AUGUST 4, 2023
";, "with": "projects/common/src/environments/environment.prod.ts" ";, "with": "projects/common/src/environments/environment.prod.ts" ";, "with": "projects/common/src/environments/environment.prod.ts"

InfoGovNuggets
OCTOBER 16, 2018
The app requests data about the patrons’ allergies. I was surprised that the restaurant quoted in the article is in California. A mobile app asks restaurant patrons to provide a bunch of information about themselves so that the restaurant can serve them better.

CGI
SEPTEMBER 30, 2015
Each quote request, whether from a software house, direct website or aggregator, is translated to native IHP format for use throughout IHP and the insurer rating tool (often polaris). Imagine what could be achieved with a centralised, total customer view including all quotes, new business, MTA’s, renewals , claims details etc.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content