Why Paying to Delete Stolen Data is Bonkers
Krebs on Security
NOVEMBER 4, 2020
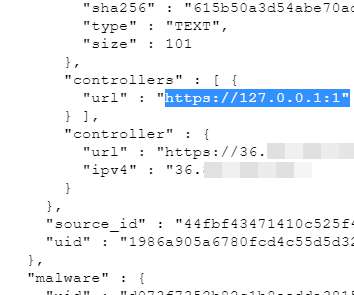
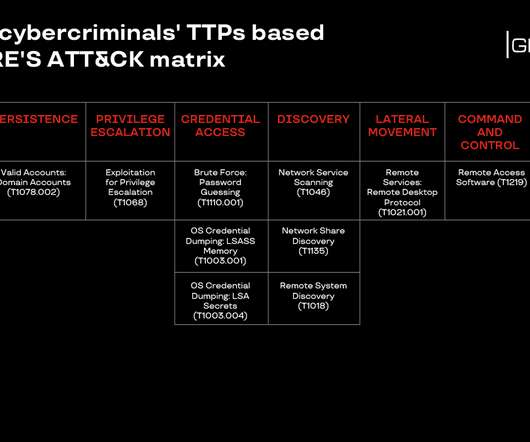
Companies hit by ransomware often face a dual threat: Even if they avoid paying the ransom and can restore things from scratch, about half the time the attackers also threaten to release sensitive stolen data unless the victim pays for a promise to have the data deleted. ” Image: Coveware Q3 2020 report.











































Let's personalize your content