Data is amazing. Your enterprise should think so too
Collibra
APRIL 12, 2021
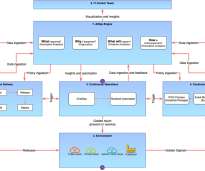
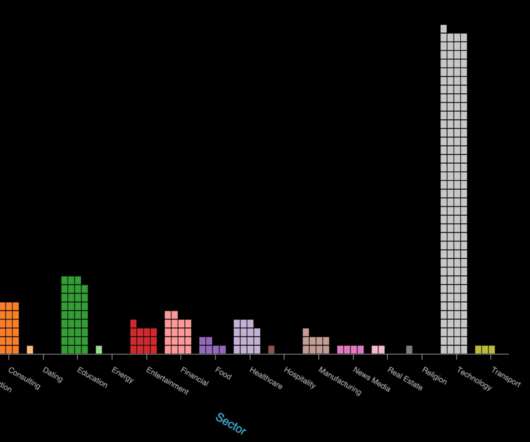
At T-Mobile, we drive successful engagement across the enterprise through strategies that can translate across many different products and systems. At Collibra’s Accelerate your data strategy in 2021 digital event, we presented our best practices for building and scaling an engaging enterprise data program. 3,472 EDGe users.












































Let's personalize your content