Lithuania security services warn of China’s espionage against the country
Security Affairs
MARCH 10, 2024
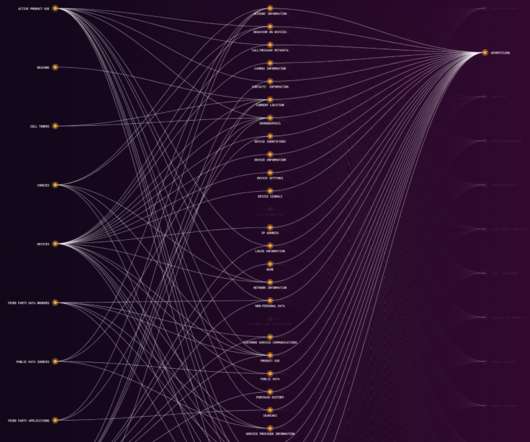
A report published by Lithuanian security services warned that China has escalated its espionage operations against Lithuania. A report released by Lithuanian security services has cautioned that China has intensified espionage activities targeting Lithuania. ” reads the report published by Lithuanian security services.
















































Let's personalize your content