What You Need to Do to Protect Your Tech Organization
Data Breach Today
JUNE 6, 2023
Beyond Identity's Husnain Bajwa on How to Be Agile and Secure in a Zero Trust World Technology and software-as-a-service, or SaaS, companies ship code at scale.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 policies shipping-policy
policies shipping-policy 
Data Breach Today
JUNE 6, 2023
Beyond Identity's Husnain Bajwa on How to Be Agile and Secure in a Zero Trust World Technology and software-as-a-service, or SaaS, companies ship code at scale.

ARMA International
SEPTEMBER 5, 2023
In the best circumstances, a well-crafted draft IG policy will sail through an approval process like a ship in warm water with strong breezes. Too often, though, the proposed policy hits an iceberg, which stops it in its tracks. Too Much Baggage The policy is bloated with non-policy statements.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
APRIL 7, 2024
More than 16,000 Ivanti VPN gateways still vulnerable to RCE CVE-2024-21894 Cisco warns of XSS flaw in end-of-life small business routers Magento flaw exploited to deploy persistent backdoor hidden in XML Cyberattack disrupted services at Omni Hotels & Resorts HTTP/2 CONTINUATION Flood technique can be exploited in DoS attacks US cancer center (..)

Armstrong Archives
DECEMBER 19, 2023
At Armstrong Archives , we’re proud to stand at the forefront of records management, offering expert guidance in record retention policy and document management, ensuring that our clients stay compliant and efficient. Also, their policies must be tailored to their specific industry requirements and business size.

Security Affairs
JULY 16, 2022
shipped with Junos Space Policy Enforcer prior to version 22.1R1. “Policy Enforcer is a component of the Junos Space Security Director user interface, integrated with Sky ATP to provide centralized threat management and monitoring for software-defined secure networks.” ” reads the advisory.

Schneier on Security
FEBRUARY 16, 2022
Differences in the amount of time it takes a vendor/product to ship a fix to users reflects their product design, development practices, update cadence, and general processes towards security reports. We hope that this comparison can showcase best practices, and encourage vendors to experiment with new policies.

Security Affairs
JANUARY 14, 2019
Zurich American Insurance Company is refusing to refund its client because consider the attack as “an act of war” that is not covered by its policy. The company declared that its shipping and invoicing was disrupted during the last four days of Q2. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Hunton Privacy
JULY 1, 2022
Carnival”), the world’s largest cruise-ship operator, for violations of the Cybersecurity Regulation (23 NYCRR Part 500) in connection with four cybersecurity events between 2019 and 2021, including two ransomware events. .

Security Affairs
DECEMBER 19, 2022
“The victim company fulfills the order and ships the goods, but the criminals do not pay for the products.” The scammer provides the actual information of a legitimate company so the credit check results in approval of the application, then the victim ships the product but never receives payment. Pierluigi Paganini.

The Last Watchdog
JULY 1, 2022
From transitioning to a work-from-home as a ‘perk’ to a ‘necessity’, the organizations had to realign their operations and do it fast, to keep the ships afloat. The pandemic-driven remote working brought about unforeseen challenges that the pre-pandemic corporate world would have never imagined. Related: Deploying human sensors.

Security Affairs
OCTOBER 9, 2022
Both UK and European Union banned on insuring ships carrying Russian oil. “At a minimum, the state backed cyber-attack exclusion must: exclude losses arising from a war (whether declared or not), where the policy does not have a separate war exclusion. .” ” reads a bulletin sent to syndicates.

Krebs on Security
NOVEMBER 23, 2018
CHCEK THE SHIPPING. Often times, items that are advertised at steeper discounts than other online stores make up for it by charging way more than normal for shipping and handling. Be careful what you agree to: Check to make sure you know how long the item will take to be shipped, and that you understand the store’s return policies.
Security Affairs
FEBRUARY 12, 2022
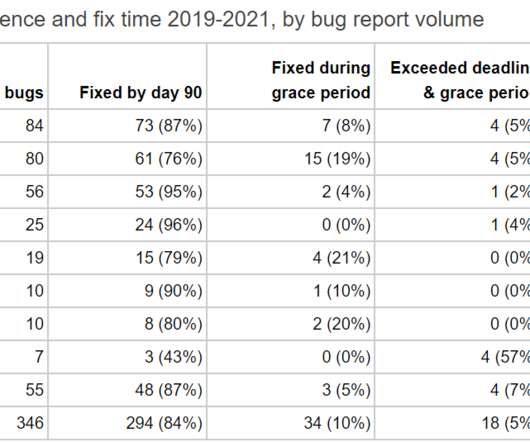
. “The first thing to note is that it appears that iOS received remarkably more bug reports from Project Zero than any flavor of Android did during this time period, but rather than an imbalance in research target selection, this is more a reflection of how Apple ships software. ” continues the report.

Krebs on Security
JANUARY 7, 2021
That intrusion involved malicious code being surreptitiously inserted into updates shipped by SolarWinds for some 18,000 users of its Orion network management software as far back as March 2020. “Due to the nature of the attacks, the review of this matter and its impact is ongoing.”

Krebs on Security
APRIL 3, 2023
“The Kenora resident is no stranger to the government as he contributed to Canada’s new Digital Charter, Bill C-11, which is a new Cyber Security policy,” reported Drydennow.com , a news website that covers Northwestern Ontario. Fake Investor John Bernard Sinks Norwegian Green Shipping Dreams

The Last Watchdog
NOVEMBER 1, 2023
Cocanower “The SEC has increased measures to ensure investment advisers adopt and implement effective cybersecurity policies,” said Michael Cocanower, founder and CEO of AdviserCyber. AdviserCyber doesn’t just ship cybersecurity software and call it a day.

Security Affairs
OCTOBER 11, 2021
The researchers speculate the attackers aimed at gaining access to commercial satellite imagery and proprietary shipping plans and logs, this information could allow the Iranian Government to compensate for its developing satellite program. ” continues the report. Block all incoming traffic from anonymizing services where possible.

erwin
JUNE 26, 2020
Beyond Amazon’s advanced search capabilities, the company also provides detailed information about each product, the seller’s information, shipping times, reviews, and a list of companion products. Clearly documents data catalog policies, rules and shares information assets. Managing a remote workforce creates new challenges and risks.

Hunton Privacy
FEBRUARY 15, 2024
Specifically, the Implementation Plan provides that financial institutions are permitted to transfer operational data outside of China pursuant to applicable security policies and measures. The latter is a new government department with the authority to conduct preliminary reviews of applications for cross-border data transfers.

The Last Watchdog
NOVEMBER 9, 2020
Too often we see companies with strong security policies and tools to protect employee corporate-owned endpoints lacking any security oversite for IoT and mobile devices,” Chris Sherman, senior industry analyst at Forrester told me. “We The operating systems of home IoT devices today typically get shipped with minimal logon security.

CILIP
DECEMBER 11, 2023
Whose retention policies do you follow? In Ministerial departments, KIM staff are working with Ministers and their Special Advisors, and need to be aware of changes in Government policies and challenges that arise. The question now is what do you do about the areas where there are several information owners jointly working?

Data Protection Report
FEBRUARY 23, 2024
Nonpublic Maritime Cybersecurity Directive The announcement also addresses certain national security concerns posed by the use of port cranes, known as ship-to-shore cranes, manufactured in the People’s Republic of China (PRC). It also incorporates the definition of “incident” from 44 U.S.C.

Security Affairs
NOVEMBER 17, 2018
Kevin Hertz, Voxox’s co-founder and chief technology officer, wrote in an email that the company is “looking into the issue and following standard data breach policy at the moment,” and that the company is “evaluating impact.” It has been estimated that the exposed archive included at least 26 million text messages year-to-date.

eSecurity Planet
JULY 13, 2021
Spam filters can be overzealous at times, which is why important emails like order confirmations and shipping updates sometimes end up in the wrong folder. It’s a customizable policy layer of email security that enables authentication technologies including the Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM).

Thales Cloud Protection & Licensing
NOVEMBER 25, 2021
Many retailers and shipping services are planning to hire temporary workers for the upcoming holiday season. This raises an important question: how are retailers, shipping services, and other organizations planning on protecting their systems from unauthorized access during this holiday surge of temporary and frontline workers?
eSecurity Planet
AUGUST 3, 2022
The software is shipped with advanced offensive capabilities that are very similar to Cobalt Strike, such as C2 (Command and Control) infrastructure, EXE and ELF implants, RAT (Remote Access Trojan), and many more. ” It’s critical to monitor endpoint activity to spot unusual processes and behaviors.

Adam Shostack
JUNE 21, 2018
And because I’m not a housing policy expert, I can miss some of the nuances and see the effect of the policies overall. In others, there are mandatory policies and review boards. We in security have fought for these mandatory policies because without them, products ignored security. They may be no prettier.

The Last Watchdog
OCTOBER 8, 2018
NotPetya , considered one of the most destructive cyber attacks, completely destroyed global shipping company Maersk’s computer network in 2017. Neray lays out the complex challenge: “At a policy level, the United States must be much more vocal and let Russia know it’s not okay to attack civilian infrastructure.

The Schedule
DECEMBER 19, 2019
The Yard was once a federal ship repair facility on the Brooklyn waterfront owned and operated by the US Navy. During WWII it was the largest industrial complex in New York state – a 300-acre facility employing 70,000 civilian workers repairing over 1,000 ships.
Security Affairs
JUNE 17, 2021
The company primarily deals in the sale and shipping of beauty products such as skincare and perfume. Pictured: Screenshots of Unishop’s privacy policy with Cosmolog listed as a co-responsible in both Turkish and English. They are owned by Gercek Kozmetik. They also sell other goods under the name “Marketlog.”.

The Last Watchdog
MAY 13, 2020
cybersecurity policy needs to match societal values CISOs must preserve and protect their companies in a fast-changing business environment at a time when their organizations are under heavy bombardment. Attests Salvi: “It is extremely important to have the right team to run your ship. Related: Why U.S.

Security Affairs
JANUARY 21, 2020
“The incident potentially involved information submitted during the final purchase process on our website, www.hannaandersson.com, including name, shipping address, billing address, payment card number, CVV code, and expiration date,” reads a notice issued by the company.

InfoGovNuggets
JANUARY 21, 2019
Or is it just a case of the ship taking on a lot of water? This is just a Governance point, with a dash of Compliance, with policy. What happens when your head of global security doesn’t follow the rules. Or the head of HR? Is something “off” about the culture?

Collibra
JANUARY 14, 2022
Data governance enables you to establish enterprise-wide policies and map them to sensitive or protected data classes for access control. Collibra ships around 40 common formats for automatic PII identification, and you can customize them or add more. The essential role of data quality in compliance.

InfoGovNuggets
NOVEMBER 7, 2018
Smugglers had in the past “hid” their ships, but that will now be harder. What controls do you need to have in place to make sure your policies are followed? Smugglers of Iranian crude will be challenged by satellites and big data. Certain companies find a business opportunity in helping to track these vessels.

Architect Security
JANUARY 25, 2021
Policy around data classification is going to dictate certain aspects of how that data must be treated. Policy and procedure for data destruction must take into account Legal and Financial data holds and retention periods. This could involve shipping or transfer to another facility. Is it proprietary source code of your product?

Data Matters
DECEMBER 21, 2020
Shipments from EU Member States or from the UK to third countries: EU exporters will no longer be able to rely on UK export authorizations granted pursuant to the EU Dual-Use Regulation to ship dual-use items from the EU to other third countries.

Schneier on Security
AUGUST 27, 2018
Editorial writers demanded that, under the administration's "zero tolerance" policy, he step aside while Congress held hearings. But the secretary could only respond weakly with a few air patrols and diversions of ships already at sea. I found this excerpt here.
eSecurity Planet
FEBRUARY 6, 2023
SEM ships with hundreds of predefined correlation rules, including authentication, change management, network attacks, and more. and system change auditing (policies, files, etc.). SolarWinds Security Event Manager (SEM) 2022.4 supports log forwarding to other applications, as well as SolarWinds SEM deployments on Azure.

Hunton Privacy
JANUARY 22, 2021
The judgment also notes that, “the policy of the GDPR is that someone who is habitually resident in a Member State should have the option to sue there rather than anywhere else. This is so even if the controller or processor has an establishment elsewhere.”
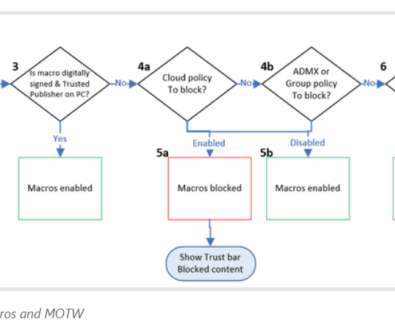
eSecurity Planet
FEBRUARY 9, 2022
For years Microsoft Office has shipped powerful automation capabilities called active content, the most common kind are macros. Microsoft is considering bringing in a group policy that will enable IT administrators to re-enable the protocol and control its use inside their organizations. Read next: Top Vulnerability Management Tools.

KnowBe4
DECEMBER 6, 2022
KCM GRC is a SaaS-based platform that includes Compliance, Risk, Policy and Vendor Risk Management modules. Quick implementation with pre-built compliance requirements and policy templates for the most widely used regulations. All you have to do is enter your credit card to cover shipping and handling–fair enough, right?

ForAllSecure
MAY 2, 2023
This includes identifying security requirements, defining security policies , and selecting the appropriate security testing tools. That said, teams adopting agile principles in how they write and ship code often see the most benefit from DevSecOps practices, due to a similarity in the principles of the two.

Data Matters
SEPTEMBER 22, 2021
To clarify the future policy position on software as a medical device (“SaMD”) and AI in the UK, the MHRA has published a new set of “work packages,” the key elements of which are to be delivered from autumn 2021 until summer 2023, with the aim of the UK becoming the “home of responsible innovation for medical device software.”.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content