Who Is Responsible for Protecting Physical Security Systems From Cyberattacks?
Dark Reading
JANUARY 14, 2021
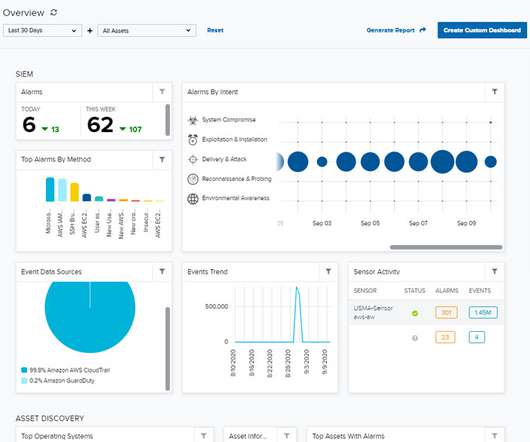
It's a question that continues to engage debate, as the majority of new physical security devices being installed are now connected to a network. While this offers myriad benefits, it also raises the question: Who is responsible for their cybersecurity?










































Let's personalize your content