ConnectWise fixed critical flaws in ScreenConnect remote access tool
Security Affairs
FEBRUARY 20, 2024
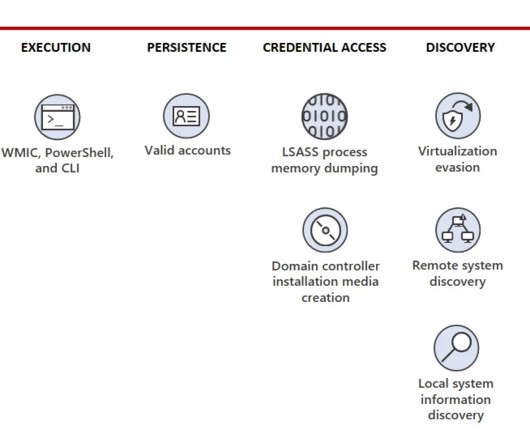
ConnectWise warns of the following two critical vulnerabilities in its ScreenConnect remote desktop access product: CWE-288 Authentication bypass using an alternate path or channel (CVSS score 10) CWE-22 Improper limitation of a pathname to a restricted directory (“path traversal”) (CVSS score 8.4) The issues impact ScreenConnect 23.9.7










































Let's personalize your content