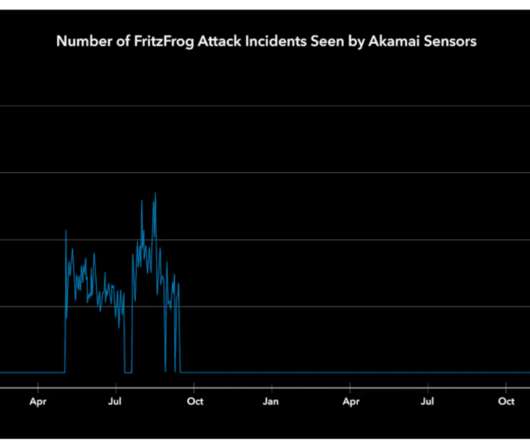
FritzFrog P2P Botnet is back and targets Healthcare, Education and Government Sectors
Security Affairs
FEBRUARY 11, 2022
The Akamai researchers developed a tool called Frogger that allow them to gather information on infected hosts, including their uptime, hashrate, peers, and hasrate, if a cryptominer is running. “The new implementation uses a public SCP library written in Golang in GitHub. ” continues the report.















Let's personalize your content