CrowdStrike discovered the first-ever Dero cryptocurrency mining campaign
Security Affairs
MARCH 15, 2023
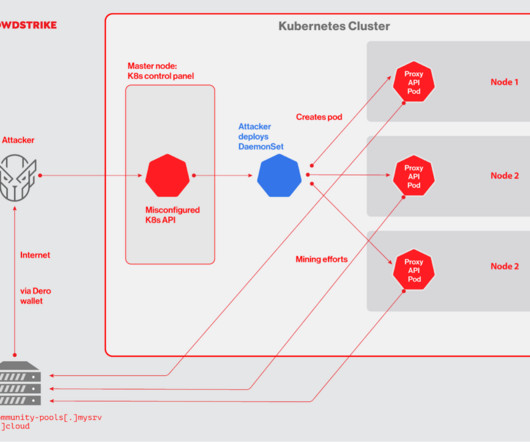
CrowdStrike researchers discovered the first-ever cryptocurrency mining campaign aimed at Dero mining since February 2023. It claims to offer improved privacy, anonymity and higher monetary rewards compared to other cryptocurrencies. The campaign started in February 2023 and originated from three servers based in the U.S.




























Let's personalize your content