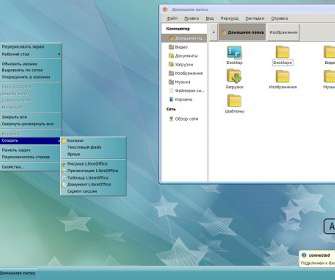
Russian military plans to replace Windows with Astra Linux
Security Affairs
MAY 31, 2019
Cyber security seems to subvert the globalization concept, governments are working to develop their own technology fearing possible espionage and sabotage activities of foreign states. The Russian military is in the process of replacing the Windows system with the Linux distribution Astra Linux. Pierluigi Paganini.





















Let's personalize your content