Panasonic Warns That IoT Malware Attack Cycles Are Accelerating
WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

Thales Cloud Protection & Licensing
FEBRUARY 28, 2022
To enable this revolution, automobile manufacturers and their supply chain partners have rapidly adopted new technologies to better serve customers and win competitive advantages: Embedding high-speed connectivity in vehicles to improve customer experience and entertainment as well as real-time diagnostics and OTA updates. Data security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JUNE 22, 2019
Trend Micro recently discovered an Android crypto-currency mining botnet that can spread via open ADB (Android Debug Bridge) ports and Secure Shell (SSH). Security researchers at Trend Micro have discovered an new Android crypto-currency mining botnet that spreads via open ADB ( Android Debug Bridge ) ports and Secure Shell (SSH).

Security Affairs
APRIL 28, 2020
The purpose of the script is to optimize the mining module by querying the information about the CPU through the reading of the “ /proc/cpu ” and when the manufacturer is retrieved the script provides to add some specific registry values depending by the vendor through the Model-Specific Register utility “ wrmsr ”. Pierluigi Paganini.

eSecurity Planet
MARCH 22, 2023
Network security protects and monitors the links and the communications within the network using a combination of hardware, software, and enforced policies. Networks and network security comes in a wide range of complexity to fit the wide range of needs. For a more general overview consider reading: What is Network Security?
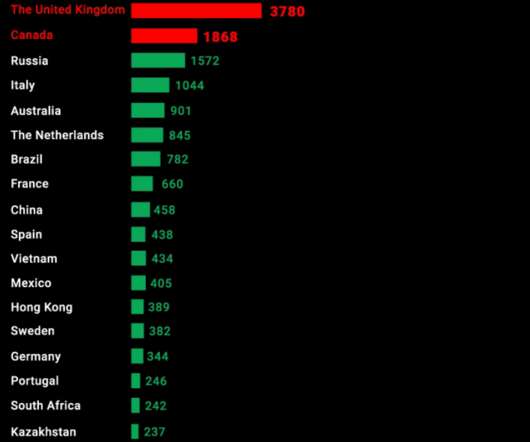
Security Affairs
MAY 12, 2021
Our research shows that large and small manufacturers are identifiable, with Aastra-Mitel topping the list. Aastra-Mitel tops the manufacturer list, the United States leads the list among countries, and London tops the chart among cities. Devices made by the US manufacturer Polycom, a subsidiary of Plantronics Inc.,

Security Affairs
SEPTEMBER 30, 2019
But let’s go back to the beginning of the story when my very good friend @0xrb found in his honeypot this new “ Mirai like ” Linux malware, which has important differences with the Mirai implementation. Odisseus – Independent Security Researcher involved in Italy and worldwide in topics related to hacking, penetration testing and development.
Let's personalize your content