Russia-linked APT28 and crooks are still using the Moobot botnet
Security Affairs
MAY 3, 2024
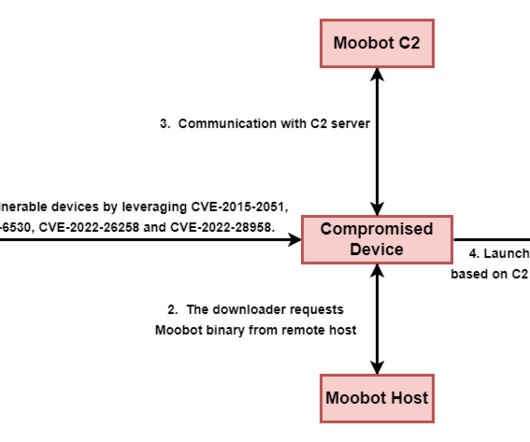
“Apart from the EdgeRouter devices, we also found compromised Raspberry Pi and other internet-facing devices in the botnet. . “We attribute the NTLMv2 hash relay attacks and the proxying of credential phishing to Pawn Storm, while the pharmaceutical spam looks to be related to the infamous Canadian Pharmacy gang.”











Let's personalize your content